Discover, monitor and manage your Crypto Posture continuously
Keys, certificates, algorithms, protocols and source code change continuously across on-premises, cloud, and hybrid environments. How do you identify the weak, expired, or misconfigured cryptographic assets?

Get started with Advance “Agentless”

What is Cryptographic Posture Management?
Enable Your Cryptographic Posture
Management with Advance
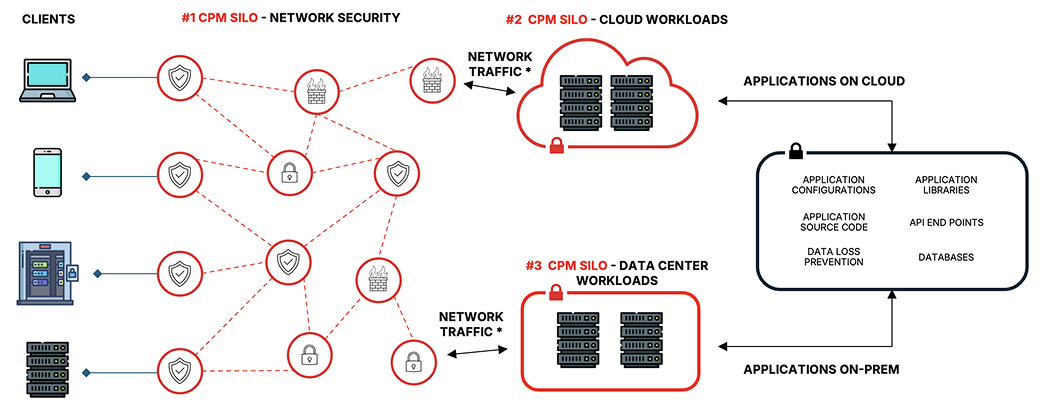
Crypto Posture Management for continuous visibility and control you need
Bring visibility to your cryptographic inventory with Advance
- Connect a configuration management database (CMDB) or an enterprise repository to understand workload names (hostnames), IP addresses
- Analyze encryption used, vulnerabilities and risk posture by assessing server workloads in the cloud and data centers using ISARA Crypto Validator
- Aggregate the metadata of keys from cloud-based key management systems, key stores, and local filesystems
ISARA Advance
Data Sources
Share crypto posture and quantum readiness with organization's' function based reports
- Executive level, sub-organization level reports
- Audit and compliance reports for NIST CSF 2.0, PCI-DSS and others
- Export reports as PDF and share
- Customize reports
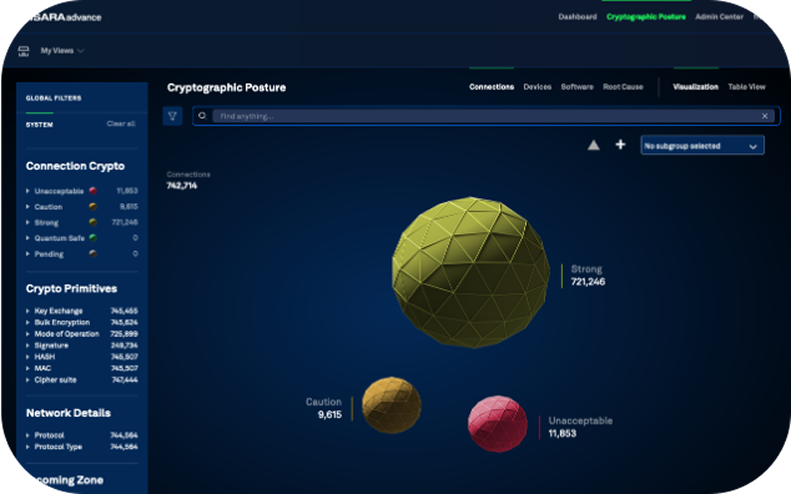
Get 360 degree context with data synchronized across enterprise systems
- Get data synchronized inbound from configuration management database or enterprise repository
- Trigger agentless execution from CRON jobs or endpoint sensors such as Tanium, Ansible
- Collect data from cloud key stores and key management systems
- Discover encryptions used in databases
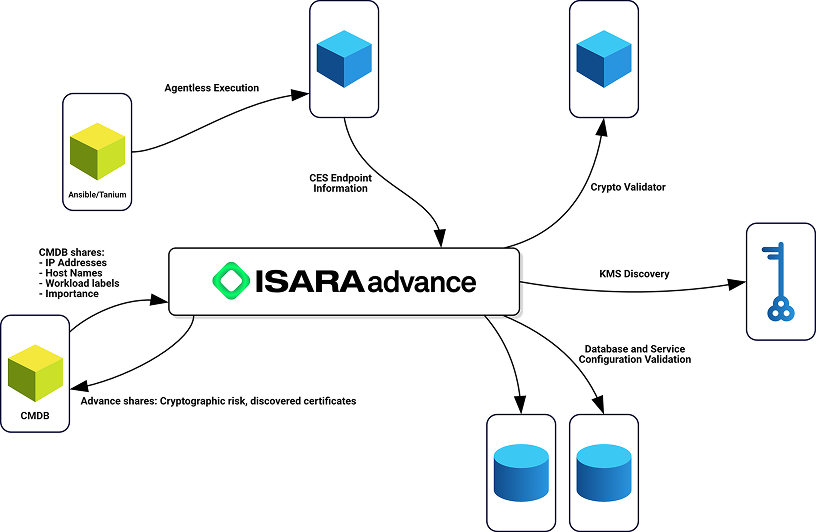
Autonomously manage crypto posture for Quantum Ready Zero Trust Architecture
- Automated integrate with workflow management to create and track progress
- Update service configurations
- Deploy updated keys to cloud and server environments
- Work with teams and vendor to migrate applications