Cryptographic Inventory and Posture Intelligence at Scale
Map your cryptography, score your posture, and reduce algorithm risk across the entire environment with ISARA Advance®
Complete visibility
Clear scoring & risk insights
Actionable & prioritized
Agentless deployment

Validate Your Architecture and Clear the Path to Agile Quantum Readiness
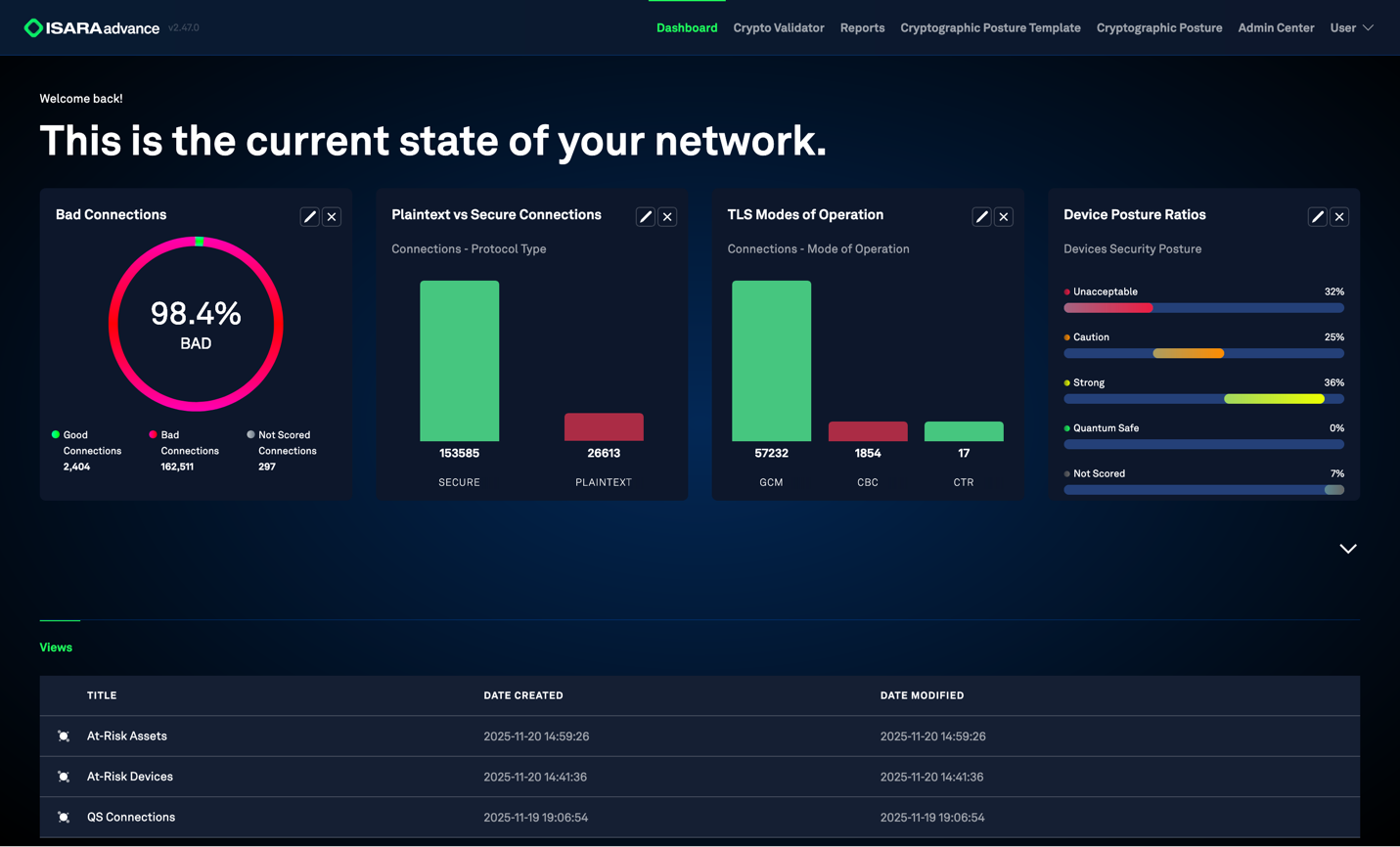
Enterprises are plagued by legacy encryption, insecure protocols, and unmanaged certificates. Advance gives you full visibility into your cryptographic posture so you can manage risks, pass audits, and enable modernization.
How ISARA Advance Works
Discover. Assess. Prepare.
A clear three-phase workflow giving teams full cryptographic visibility, contextualized business risks, and prioritized remediation recommendations. Without agents. Without phoning home.
DISCOVER
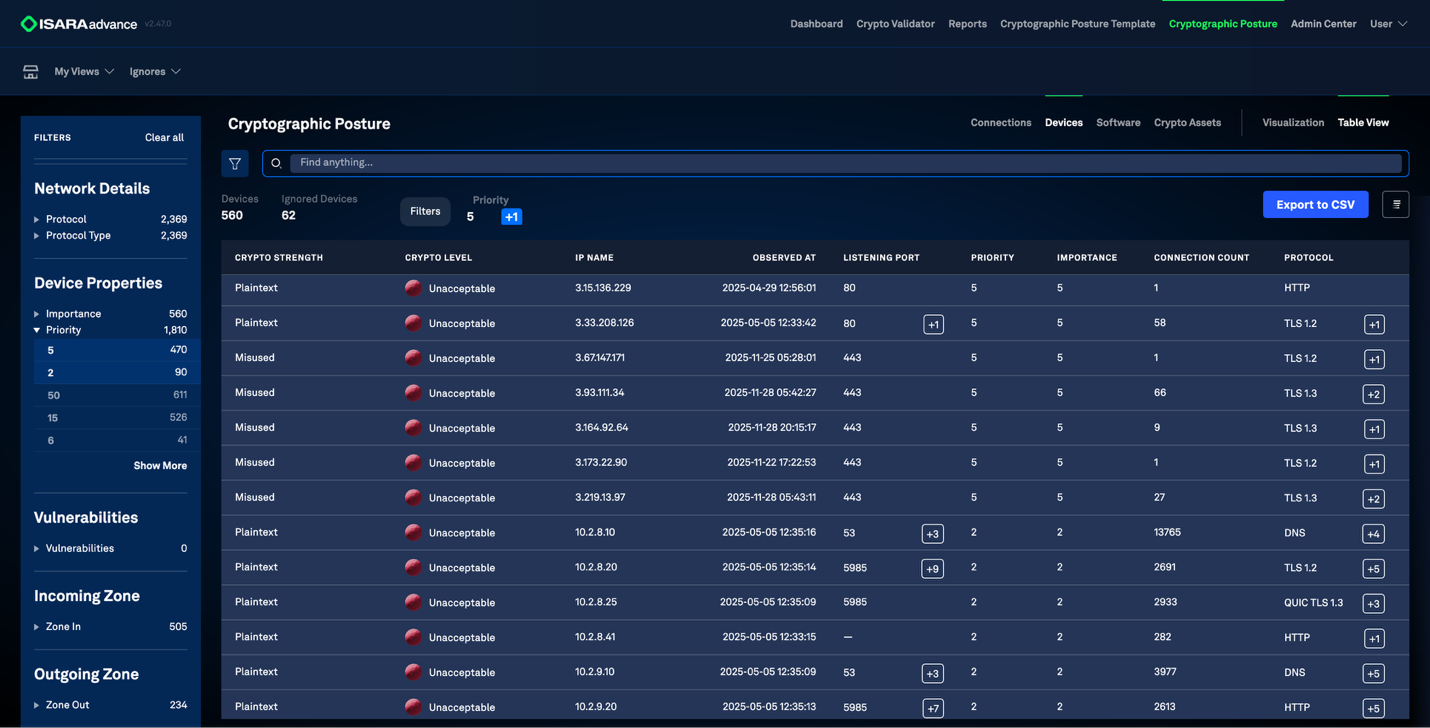
Complete Cryptographic Mapping
Agentless-first discovery builds a real-time inventory of your cryptography across cloud, on-prem, and hybrid environments.
-
Visibility for executives and analysts into all vulnerable protocols and modes of operation.
-
Inventory algorithms, protocols, primitives, key lengths, and device information.
-
Identify certificate locations, owners, status, and usage risks across your network.
Assess
Exposure & Posture Analysis
Automated scoring highlights the weaknesses that impact compliance, resilience, and long-term security.
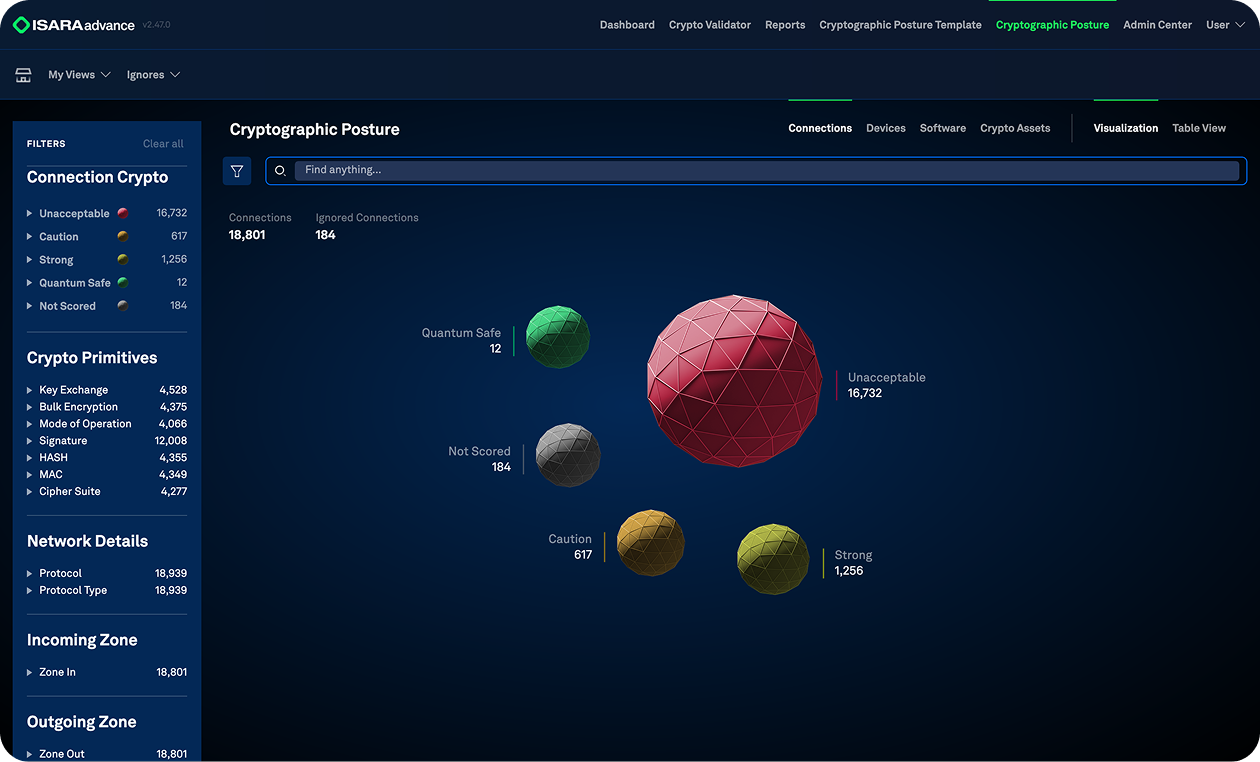
-
Validate your architecture and know what devices are connecting to your critical servers.
-
Flag deprecated or weak algorithms like vulnerable RSA and ECC implementations.
-
Detect expired, misconfigured, and rogue certificates that undermine integrity and trust.
Prepare
Remediation & Modernization
Translate discovery and risk insight into prioritized remediation steps that strengthen your cryptographic posture and prepares you for your PQC migration.
-
Remediate vulnerabilities through ticket-based workflows and CMDB integrations.
-
Prioritized remediation actions based on risk and impact.
-
Build a quantum-ready foundation with clear modernization steps.
Integrate Crypto Posture Management into Your Security Stack
Advance integrates with your existing security, infrastructure and certificate systems to centralize discovery, posture scoring and remediation.
Security Stack
SIEM Platforms NDR / Network Detection EDR TelemetryInfrastructure
Cloud Environments CMDB / Asset Inventory ToolsCertificate & Identity
Certificate Management Systems Public Key InfrastructureDeveloper Tools
DevOps / CI Pipelines Key Management SystemsCryptographic Risks Are Already in Play
Outdated algorithms and insecure protocols can be exploited today. Blind spots and unmanaged certificates only heighten the risk. And sensitive data encrypted by quantum-vulnerable algorithms are being harvested for future decryption. Before these live risks can be dealt with, organizations need to validate their current cryptographic architectures.
Assess Your RiskVulnerabilities Need Context
Too often, cryptographic vulnerabilities don't get remediated because the contextual business risk is not understood.
Risks Exist Today and Tomorrow
Data is not only vulnerable to Harvest-Now, Decrypt-Later attacks. Weak encryption can be broken now, and long-lived credentials are ripe for future forgery.
Visibility Closes Compliance Gaps
Compliance requirements demand complete inventories. Organizations are risking audit failures, downtime, and penalties.
How ISARA Advance Strengthens High-Risk Industries
The ISARA Advantage
Deployment and Environment Guidance
Support for setting up discovery across hybrid, cloud and on-prem environments based on your architecture.
Posture Interpretation & Expert Review
Assistance understanding posture scoring, algorithm risk patterns and modernization priorities.
Integration Support With Existing Tools
Help connecting Advance insights to SIEM, NDR, EDR and certificate management systems.
Standards & Compliance Alignment
Guidance tied to NIST PQC, audit expectations and cryptographic policy updates.
Take Control of Your Cryptography Before It's a Liability
Advance gives you visibility, scoring, and targeted remediation actions so you can reduce exposure and prove control when it matters most.