ISARA Insights Blog
Tags:
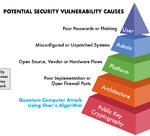
How Quantum Computing’s Threat to Security is Different from All Other Security Breaches
The quantum threat represents the first time in history that a cybersecurity breach will be the result of a complete break of modern public-key cryptography. For many, this information might come as a surprise. There seems to be a new security breach almost every day; in January 2018 a bug was discovered…

Quantum Computing: Its Emergence & Implications on Information Security
Leading governments around the globe, along with major corporations, including IBM, Google, Microsoft, have all made substantial investments in the development of large-scale quantum computers, just in the past decade. There's a reason for this prescient obsession. What exactly is quantum computing? Quantum…

The Quantum-Safe Migration: Cryptography’s Overhaul
On October 17th, the Hudson Institute – a think tank headquartered in Washington, DC – gathered quantum computing and cybersecurity experts to explore the quantum threat from a security and policy perspective. Mentioned several times throughout the event was the migration to a quantum-safe state. This…

Do You Know About Quantum’s Threat to OTA Software Updates?
Today, remotely updating a device’s software - such as a connected car or smartphone - is easy and cost-effective. There’s no need to physically return the device to the manufacturer, which happily saves everyone time and valuable resources. However, within the decade, remote or over-the-air (OTA)…

FinDEVr London 2017: Scott Totzke Talks About the Quantum Opportunity and Threat
On June 12, ISARA's CEO & Co-Founder, Scott Totzke, was at FinDEVr London 2017 to talk about the emerging quantum computing threat to cybersecurity standards that global financial institutions, as well as governments and businesses, rely on today. Scott explains quantum supremacy: what it means and…