ISARA Insights Blog

Cybersecurity in the Age of Quantum Computing: A Cryptographer’s Call to Action
Computing power has advanced far beyond the invention of the transistor. Today’s digital infrastructures rely on public-key cryptography to safeguard commerce, state secrets and personal privacy. But a new paradigm is within our view. Quantum computers utilize superposition and entanglement to perform…
Tags:

Mastering the Quantum Challenge for Machine Identities
It is no secret that cybersecurity threats are ever-evolving. Each day, security professionals around the world receive reports of new vulnerabilities, new attack vectors, and new challenges that need to be overcome in this increasingly connected world. To make matters worse, cyberattacks are not only…

Microsoft’s CryptoAPI flaw/CurveBall: a teaser of the quantum threat
The National Security Agency recently discovered a major cryptographic flaw in Microsoft’s low-level code within their operating system. This flaw, now known as CurveBall, was found within Windows CryptoAPI and effects the way Elliptic Curve Cryptography (ECC) x.509 certificates are validated, giving…
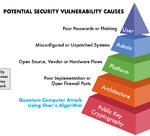
How Quantum Computing’s Threat to Security is Different from All Other Security Breaches
The quantum threat represents the first time in history that a cybersecurity breach will be the result of a complete break of modern public-key cryptography. For many, this information might come as a surprise. There seems to be a new security breach almost every day; in January 2018 a bug was discovered…