ISARA Insights Blog
Featured Blog Post
Your Post-Quantum Cryptography Journey: Over the River and Through the Woods
Paul Lucier
Dec 08, 2021
‘Tis the season for visits to grandmother and Uncle Joe. ‘Tis also the season for organizations to start planning their roadmaps for a quantum-safe New Year. After all, the third round of the NIST PQC Standardization Process is expected to be completed in early 2022 when the National Institute of Standards and Technology (NIST) makes the much-anticipated announcement of the post-quantum algorithms it intends to standardize.

Tags:
Your Post-Quantum Cryptography Journey: Over the River and Through the Woods
Paul Lucier
Dec 08, 2021
‘Tis the season for visits to grandmother and Uncle Joe. ‘Tis also the season for organizations to start planning their roadmaps for a quantum-safe New Year. After all, the third round of the NIST PQC…

Mastering the Quantum Challenge for Machine Identities
Mike Brown
Nov 11, 2020
It is no secret that cybersecurity threats are ever-evolving. Each day, security professionals around the world receive reports of new vulnerabilities, new attack vectors, and new challenges that need…

Microsoft’s CryptoAPI flaw/CurveBall: a teaser of the quantum threat
Mike Brown
Jan 17, 2020
The National Security Agency recently discovered a major cryptographic flaw in Microsoft’s low-level code within their operating system. This flaw, now known as CurveBall, was found within Windows CryptoAPI…

How Quantum Computing’s Threat to Security is Different from All Other Security Breaches
Mike Brown
Jan 11, 2018
The quantum threat represents the first time in history that a cybersecurity breach will be the result of a complete break of modern public-key cryptography. For many, this information might come as a…
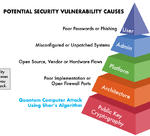
The Quantum-Safe Migration: Cryptography’s Overhaul
Scott Totzke
Oct 26, 2017
On October 17th, the Hudson Institute – a think tank headquartered in Washington, DC – gathered quantum computing and cybersecurity experts to explore the quantum threat from a security and policy perspective.…
