ISARA Insights Blog
Featured Blog Post
Myth-Busting the Quantum Threat: The Top 3 Misconceptions About Quantum-Safe Migrations
Paul Lucier
Jul 23, 2019
Part of our mission at ISARA is to educate and raise awareness of the security risks introduced by large-scale quantum computing. Since I joined ISARA in 2016, I’ve spoken to individuals, enterprises, and governments around the world, and along the way, I’ve heard some incorrect assumptions about the impact of the quantum threat and what can be done about it today.

Tags:
Myth-Busting the Quantum Threat: The Top 3 Misconceptions About Quantum-Safe Migrations
Paul Lucier
Jul 23, 2019
Part of our mission at ISARA is to educate and raise awareness of the security risks introduced by large-scale quantum computing. Since I joined ISARA in 2016, I’ve spoken to individuals, enterprises,…

5 Ways Quantum Computing Will Change the World
Martin Laforest
Apr 17, 2019
In the days after I resigned from my position as the senior manager of scientific outreach at the Institute for Quantum Computing to join ISARA Corporation, one esteemed colleague after another would offer…

Quantum Key Distribution and Quantum-Safe Cryptography: two (complementary) approaches to becoming quantum-ready
Martin Laforest
Nov 29, 2018
Every advancement in quantum computing brings us closer to the positive and negative disruptions this revolutionary technology promises. Though a large-scale quantum computer is not here yet, its future…

How Quantum Computing’s Threat to Security is Different from All Other Security Breaches
Mike Brown
Jan 11, 2018
The quantum threat represents the first time in history that a cybersecurity breach will be the result of a complete break of modern public-key cryptography. For many, this information might come as a…
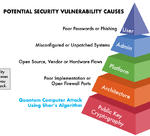
The Quantum-Safe Migration: Cryptography’s Overhaul
Scott Totzke
Oct 26, 2017
On October 17th, the Hudson Institute – a think tank headquartered in Washington, DC – gathered quantum computing and cybersecurity experts to explore the quantum threat from a security and policy perspective.…
