10 Reasons Why Cryptographic Management is Critical
Why is cryptography suddenly becoming such a big topic? Let’s face it. Cryptography has been at the core of every secure transaction since the dawn of the Internet — unassuming and low profile, it has been working its security magic all the way from hardware to apps. Public key cryptography, to be more exact, ensures the authentication and identity of all transactions and participants in the digital world — every modern business depends on it every second. Yet, we know that organizations don’t have a good handle on the location of all the cryptography deployed throughout their infrastructure, or how healthy it is. The reason is simple — for the most part cryptography has never been in the limelight, something that needed special attention. Aside from symmetric key management systems (those that encrypt databases), cryptography has been one of those unmanaged technology buckets that have been taken for granted. Buckle up, as that is about to drastically change...
This brings us to the buzz around crypto agility and the main reason that is driving it: the looming quantum threat. The question is not whether it will render the “classic” public key cryptography obsolete, but what each enterprise will do about it when the new public key cryptographic standards are released as soon as next year - in 2022 - by NIST. This massive crypto migration is inevitable and cannot be conveniently swept under the my-successor's-problem rug.
With all this trickling up to the board level, some organizations have already elevated the importance of cryptographic health with the creation of cryptographic centers of excellence (CCoE). But what do enterprises really need to know now? Why is it so important for enterprises to be aware of their cryptographic assets? And how can they make the case to the C-Suite for more funding and resources for better cryptographic management?
Here are 10 reasons why prioritizing cryptographic management is critical:
- Operating cryptography — being truly on top of it end-to-end — is a very complex and convoluted undertaking, it is infeasible as a manual task, and most enterprises cannot manage it themselves.
- The emerging quantum threat brings cryptography management to the forefront and boards are not asking their CISO when the threat will manifest itself, but what their plan of action is.
- The past has shown that cryptographic migrations, even when limited to a single cryptographic algorithm, are complicated endeavors that can take years and decades.
- The critical first step is the good old visibility — we must discover the cryptography (and that is much broader in scope than discovering digital certificates) used across the enterprise, so we can start building the corporate migration plans, and track them over time. If you have any doubts, check out NIST’s set of recommendations.
- Likewise, inventorying and categorization of discovered cryptography tends to be a tedious, manual process. The use of purpose-built tools is mandatory for any kind of success here.
- Cryptographic agility — the ability to migrate between crypto standards without the business disruption and in a cost-effective way — needs to become a priority among enterprises. Otherwise, organizations face security issues, loss of compliance, and various sources of extra cost.
- What systems are at risk? Any type of transaction that relies on public-key cryptography, which is just about all of them.
- There is often a lack of centralized management and enforcement of crypto governance and a lack of efficient cryptographic audit capabilities. This problem is solved with an enterprise-grade solution.
- Cryptographers are in high demand and in low supply.
- Cryptographic teams can build the case for more resources and funding for cryptographic upgrades and migration through audits and executive reports.
I addressed this topic in my recent Quantum.Tech presentation, Understanding the Current State of the Art in Securing Your Networks from Quantum Threats, held earlier this year.
Do you need help making the case to your C-Suite for more resources for your cryptographic management efforts? Do you need help with your enterprise’s cryptographic management? Here at ISARA, we provide crypto-agile and future-proofing solutions to help organizations in all industries protect their mission-critical assets now and in the future.
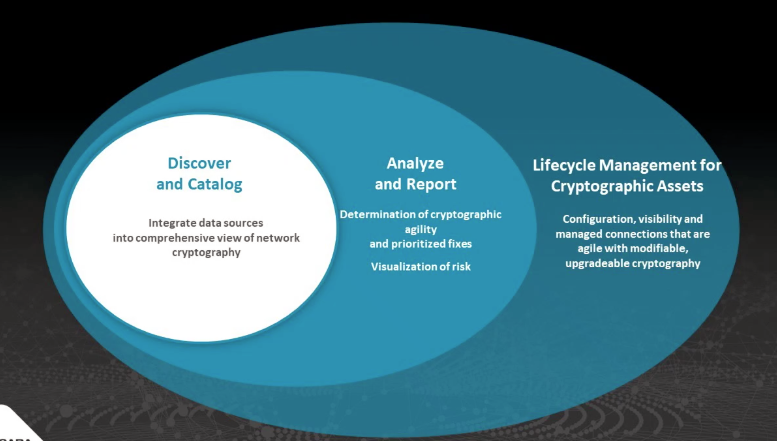
The three steps to cryptographic management. Source: ISARA.