ISARA Advance® Cryptographic Inventory and Risk Assessment Tool
Introducing a cryptographic management platform that reveals your blind spots, discovers bad usage, and equips you to act
Cryptography is the foundation of authentication and confidentiality — consequently, it’s a critical enabler of digital security.
To secure your systems today, to keep them secure tomorrow, and to comply with increasingly stringent regulations and audits, your cryptographic infrastructure needs to be understood, inventoried, and upgraded whenever necessary — without disrupting normal operations.
That’s why we created ISARA Advance: a cryptographic inventory platform that enables you to discover your cryptographic infrastructure — all from an easy-to-understand and easy-to-use central dashboard.
Advance provides inventories and assessments of the cryptography protecting data-in-motion
Bringing clarity and order to the often-overwhelming operational responsibility of managing cryptography
Advance increases cryptographic visibility and manageability, equipping you to:
- Make informed decisions about your cryptography
- Manage cryptographic risks to prevent data breaches and other disruptive incidents
- Conduct comprehensive upgrades effectively and efficiently
- Comply with regulations for data management
- Satisfy audit requirements, quickly and easily
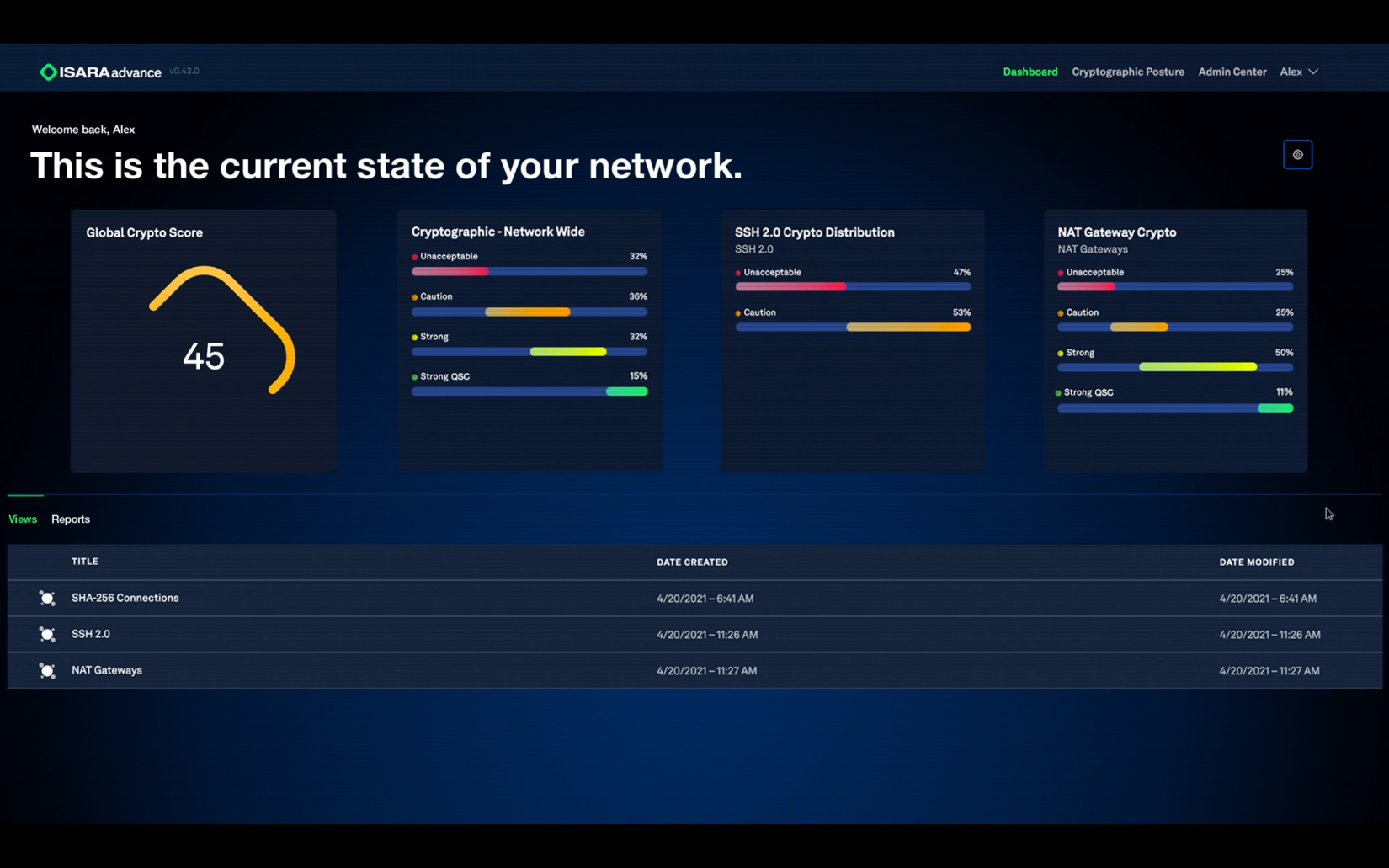
ISARA Advance simplifies cryptographic discovery and risk management
Inventorying cryptography usage, and understanding and managing the associated risks is notoriously expensive and error prone, because it's highly manual, specialized, and complex — and many organizations find themselves ill-prepared for these important projects. Here are some of the ways Advance can help.
| Advance… | So you can… |
|---|---|
|
Discovers and catalogs your cryptographic assets |
Inventory the encryption, digital signature, key-agreement, and hashing algorithms upon which your enterprise depends |
|
Surfaces existing cryptographic problems and risks |
Prioritize remediation of old and outdated algorithms, faulty configurations, and implementations |
|
Equips you to manage your cryptographic assets |
Verify which cryptographic systems are not in compliance with internal policies, cybersecurity best practices, and regulatory guidelines |
To help CIOs, CISOs, and IT teams make informed decisions, Advance organizes information and insights within a sophisticated — but elegant — dashboard featuring clear, context-rich visuals.
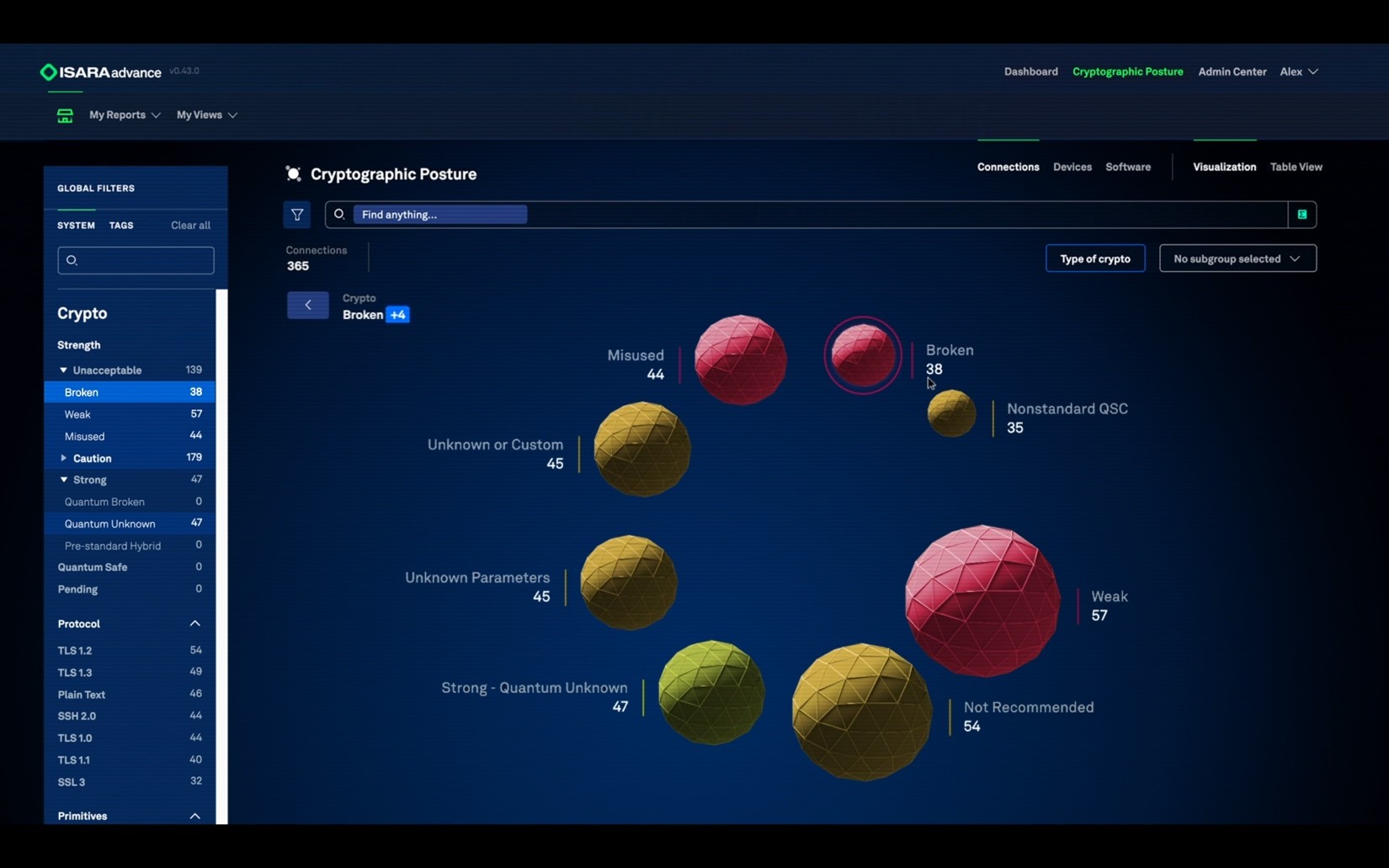
ISARA Advance reveals — at a glance — important information; in this example, Advance is showing a high-level view of the strength of the cryptography used in the enterprise’s connections
Agentless Architecture: Advance integrates into and ingests data from the NDR and EDR solutions you already have
To enable disruption-free deployments, Advance integrates into existing network detection and response (NDR) and endpoint detection and response (EDR) solutions. By utilizing and enhancing the data these tools already collect, Advance allows you to learn about your cryptographic assets without needing to deploy and manage any additional agents.
For the latest details about NDR and EDR integration, please contact us at advance@isara.com.