ISARA Radiate™ Quantum-safe Toolkit
Quantum-safe cryptography: the next generation of cybersecurity
The ISARA Radiate™ Quantum-safe Toolkit is a high-performance, lightweight, standards-based quantum-safe software development kit, built for developers who want to test and integrate next-generation post-quantum cryptography into their commercial products.
Developers choose ISARA Radiate because of the professional tools and documentation, timely product releases and updates, and thorough testing. All backed by our team of embedded security experts available to assist you with your questions and custom integration needs.
License our optimized, proprietary implementation of NIST-approved Post-Quantum Cryptography (PQC) algorithms with confidence knowing it is free from copyleft licensed code, reducing your risk of accidentally exposing your intellectual property to the public domain.
Key Benefits
Accelerate Time to Market
- Give your development team the freedom to focus on product innovation and leave the implementation of quantum-safe cryptography to us
- Test how quantum-safe cryptography fits into your products today and get your next-generation-secure products to market, faster
Developer Friendly
- Intuitive APIs let you quickly leverage the quantum-safe library, written in highly portable C99 for various platforms and architectures
- Exhaustively tested and thoroughly documented, with sample code provided
HSS & XMSS: Production-Ready for Roots of Trust and Code Signing
- Standardized in NIST SP 800-208, based on RFC 8391 and RFC 8554
- Small public keys and comparable performance to ECC-based signature schemes
- Includes ISARA’s proprietary approach to state management of the large, stateful private keys
Embedded Ready
- Bring Post-Quantum Cryptography to the embedded platform of your choice
- Run quantum-safe algroithms on constrained hardware, such as smartcards
- Execute cryptographic operations in the ARM TrustZone using OP-TEE
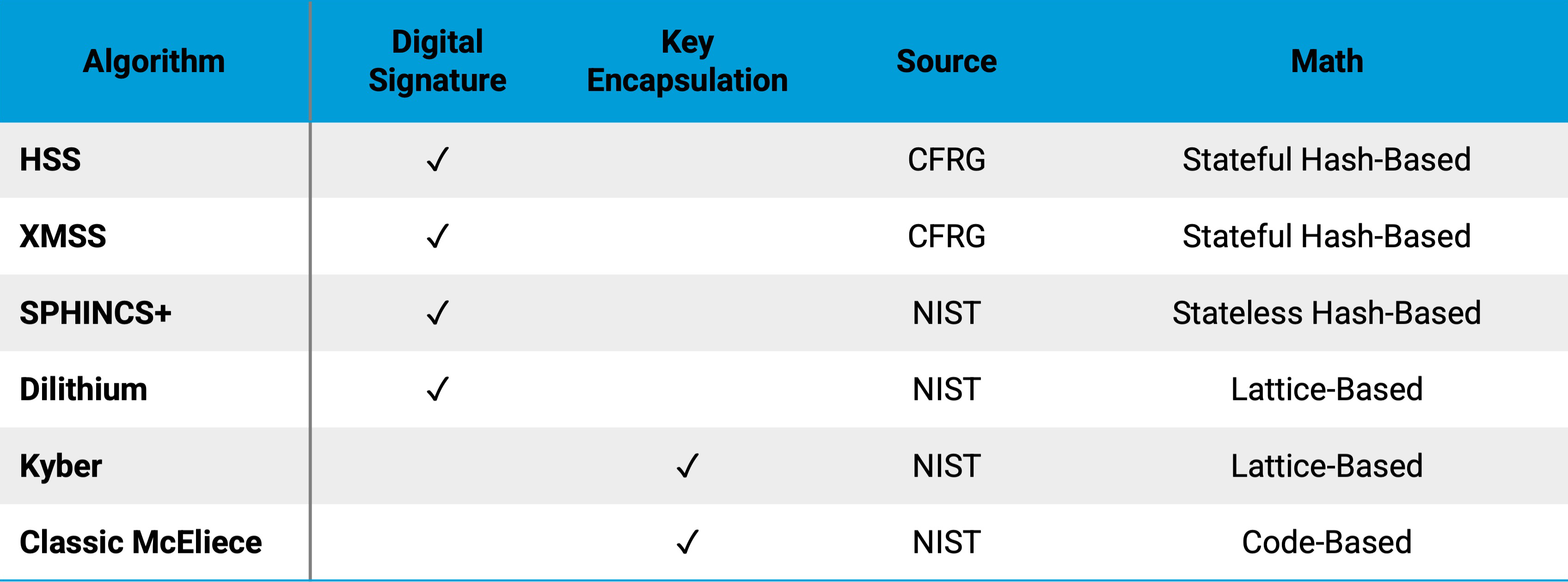
ISARA Radiate Cryptographic Library Version 3.1 Includes The Following Quantum-safe Algorithms
Services & Support
Professional Services
Our experienced team of embedded security experts can help you integrate quantum-safe security into your products as a professional services project.
Developer Support
We offer a variety of different support packages to suit your specific needs. Please get in touch with our team for more details or to discuss custom packages.
Product Updates
We regularly update the toolkit to align with globally-recognized standards and to provide improvements and optimizations. Receive the latest version backed by developer support with a commercial license agreement.
Create Quantum-safe Products Using the Toolkit Global Security Leaders Trust
Request a meeting to get started.
Are You a Developer?
We’ve created these materials just for you.