How Quantum Computing’s Threat to Security is Different from All Other Security Breaches
By Mike Brown, Chief Technology Officer & Co-Founder, ISARA Corporation
Published on Jan. 11, 2018
Updated Oct. 17, 2018
The quantum threat represents the first time in history that a cybersecurity breach will be the result of a complete break of modern public-key cryptography. For many, this information might come as a surprise.
There seems to be a new security breach almost every day; in January 2018 a bug was discovered in Intel’s chips affecting most computers, and since then several other significant breaches and alarming cybersecurity statistics were announced. Yet modern public-key cryptography such as RSA and elliptic-curve cryptography (ECC) - the very foundation of cybersecurity - haven’t been broken via an efficient attack on commercialized products when implemented correctly.
So where are today’s security breaches occurring? And how is quantum computing’s threat to security different?
The various layers of cybersecurity attacks can be broken down into five categories:
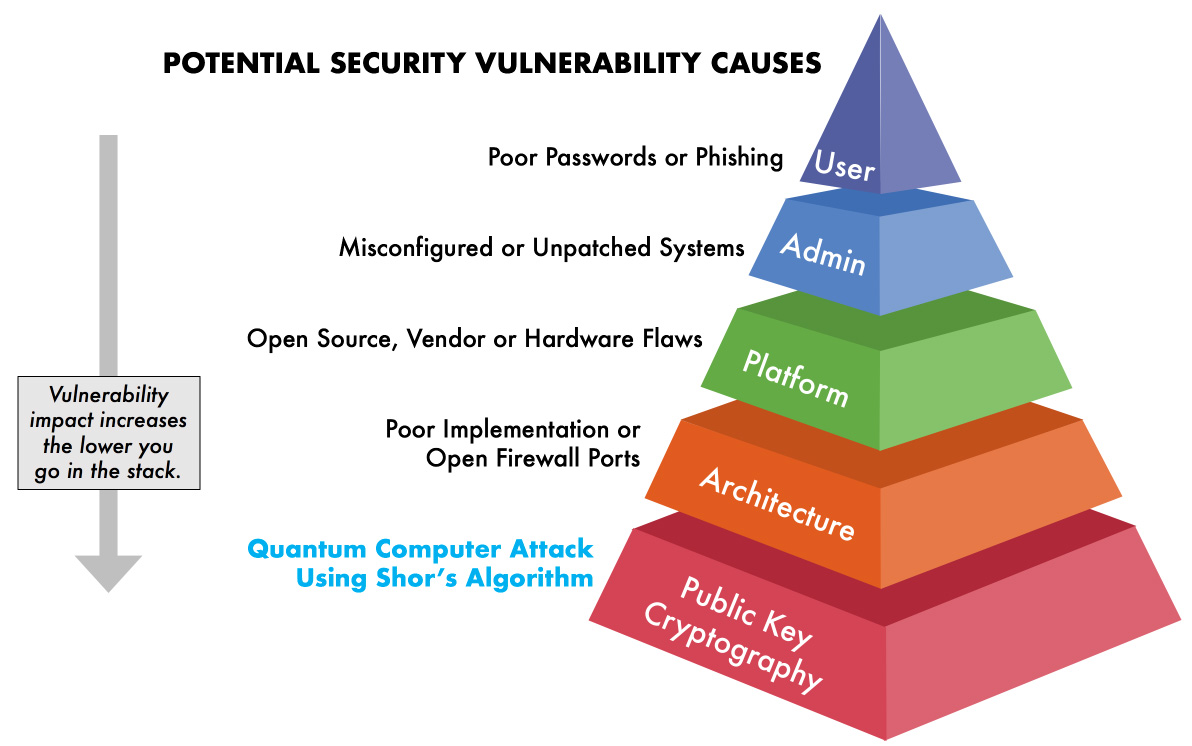
Currently, all security breaches fall into one of the top four layers of the stack. At the very foundation are modern public-key cryptosystems such as RSA and ECC. The mathematics they’re built on have remained secure against brute force attack since their discovery decades ago (RSA was first published in 1977, over 40 years ago). However, with the development of a large-scale quantum computer modern public-key cryptosystems will be compromised, creating vulnerabilities at the very core of information security.
We’ll see that as we progress down through each layer of security infrastructure, system vulnerabilities become more difficult to exploit but also have the potential to have a larger impact on critical components if it is.
1. User Error
We don’t like to blame ourselves but alas, almost 90% of all cyber claims stem from some type of human error or behaviour. In the context of corporate cybersecurity, phishing scams, social engineering, lost devices, easily guessed passwords, and using personal email for work are just some of the ways that employees fall victim to online attacks. Luckily, individual users have very few privileges, limiting the scope of a cyber attack.
2. Administrator Error
System administrators have much more responsibility. Therefore, their errors can lead to greater data breaches. For example, the highly publicized Equifax breach was caused by an unpatched system. However, In this case, the flaw was known and a patch was provided two months prior to the breach. Due to the administrator's failure to update the system in a reasonable time, the sensitive data of over 143 million people were exposed.
We’re only at the second layer, and yet, it’s easy to see how the impact of a security breach escalates the further down the stack the vulnerability is found.
3. Platform Issues
A security flaw in widely-used software could be disastrous. Heartbleed, a buffer over-read flaw in the OpenSSL cryptographic library, compromised approximately 66% of the internet in 2014. The 2018 Spectre and Meltdown vulnerabilities showcase the impact of issues at a chipset level. Implementation flaws such as these have resulted in the most significant hacks in history. In comparison, the Equifax breach doesn’t come close to this scale.
4. Architecture Flaws
With systems consistently becoming more connected, the number of endpoints that can be exploited is increasing. For example, cars are no longer merely mechanical. Instead, they have an entertainment system, local wireless networks, button activated ignition, sensor-controlled brakes and acceleration, and even autonomous systems. They are a computer on wheels. And in 2015, a hacked Jeep Cherokee showed us just how vulnerable poorly designed systems could be. White hat hackers were able to gain access to the entertainment system remotely and laterally connect to the engine and brake systems of the vehicle.
In this case, poor architecture design led to a product that, if hacked, could physically put lives at risk.
5. Public Key Cryptography
Modern public-key cryptography is at the very core of information security. Cryptosystems such as RSA and ECC provide the foundation of trust for all networks, applications and digital communications. Simply put, modern cryptography utilizes hard math problems that have been studied for decades to secure sensitive information. For example, RSA relies on the practical difficulty to factor a product of two large prime numbers. These hard math problems have never been broken, maintaining the integrity of our RSA and ECC cryptosystems. Since an adversary has not been able to solve these algorithms, cyber attacks had to come from exploiting vulnerabilities higher up the stack as we’ve explored.
However, a large-scale or “cryptographically relevant” quantum computer will be able to solve the hard math problems that secure our cryptosystems. This will make vulnerable the very foundation of information security.
A large-scale quantum computer threatens our cybersecurity by effectively breaking current public-key cryptosystems
The advent of a large-scale quantum computer will have a catastrophic effect on information security, effectively breaking the foundation of digital trust. This isn’t one organization failing to patch their systems like Equifax, or major commercial products with poor architecture, or even specific vulnerabilities compromising 66% of the internet. This is because every cybersecurity breach seen in the past has occurred somewhere in the top four layers of the stack. At the very foundation, a break in modern cryptosystems will make past vulnerabilities seem trivial. All devices, systems, and networks will be affected. Data breaches will occur on a scale much higher than anything seen before.
Migrating to quantum-safe cryptography is essential, but will take several years
Since public key cryptography is so ubiquitous and invisible, seamlessly migrating systems to quantum-safe cryptography will take years due to the vast number of end-points and systems requiring an upgrade. By creating a migration plan now, organizations and governments can prepare for the quantum threat without affecting their bottom line or end-user experience.
It’s time to begin your quantum-safe migration
Embedding quantum-safe cryptography will not prevent adversaries from exploiting user and administrative errors, poor system design, or software flaws. It will, however, protect your organization against attackers with access to a large-scale quantum computer, such as nation-states or state-funded hackers, preventing one of the potentially largest data breaches governments and organizations may see to date.