All Aboard the Quantum Migration Train
Standards bodies, government organizations, and research centers weigh in on preparing for the threat that quantum computers pose to encryption. Take action now? Don’t worry about it yet? Or, get on the quantum migration train now starting with planning and crypto-agility solutions?
The NIST National Cybersecurity Center of Excellence (NCCoE) has set in motion several practices “to ease the migration from the current set of public-key cryptographic algorithms to replacement algorithms that are resistant to quantum computer-based attacks,” according to its latest article, “Crypto Agility: Considerations for Migrating to Post-Quantum Cryptographic Algorithms.”
“Waiting around for quantum tech to mature could mean organizational change occurs too late,” cautions Deloitte’s Center for Government Insights, in its Nextgov article, “Preparing for the Coming Quantum World (Pragmatically).” Especially when it comes to government organizations and national security. Authors Adam Routh, Joe Mariani, Akash Keyal, and Scott Buchholz state that “such a revolutionary method of computing offers a whole new set of military and scientific possibilities – as well as challenges.”
The possibilities of quantum technology are as endless as a quantum key length. Consider satellite communications. Quantum computing promises an even more secure method of sending and receiving information by manipulating particles, according to the Deloitte researchers. In a military scenario, quantum radars could better detect stealth aircraft.
But before we realize all the positive potential, the researchers with Deloitte’s Center for Government Insights advocate that organizations start taking defensive action, “There are real dangers to inaction – such as the potential for adversaries to steal data now and wait to decrypt it once enough quantum computers come online.”
This espionage practice is called Harvest and Decrypt. If encrypted sensitive data is stolen today, it can be “saved” and will be accessible once a sufficiently-powered quantum computer is available. If the sensitive data has a secrecy obligation that extends beyond the time it will take to introduce large-scale quantum computing, then that data should be considered at risk today. For example, if classified information must remain confidential for 7+ years, then organizations need to consider it at risk now. Nation-state and state-sponsored attacks are on the rise. They represented 23% of data breaches in 2019, up from 12% in 2018, according to findings from Verizon's 2019 Data Breach Investigations Report (DBIR). A quarter of all breaches were associated with espionage.
NIST concurs. Once quantum computers are in place, “individuals can record and capture current information and communications and gain access to the raw content once quantum computing technology is available. This includes all recorded communications and stored information protected by those public-key algorithms.”
Scott Totzke, CEO, here at ISARA, reiterates that quantum technology will have a tremendous effect on organizations’ trust infrastructure. Imagine a pyramid, with cryptography at every layer – the glue holding everything together. Today’s exploits generally happen in the top layers: users, admin. With quantum computing, the most trusted elements – identity infrastructure, platform, architecture – become easier to attack.
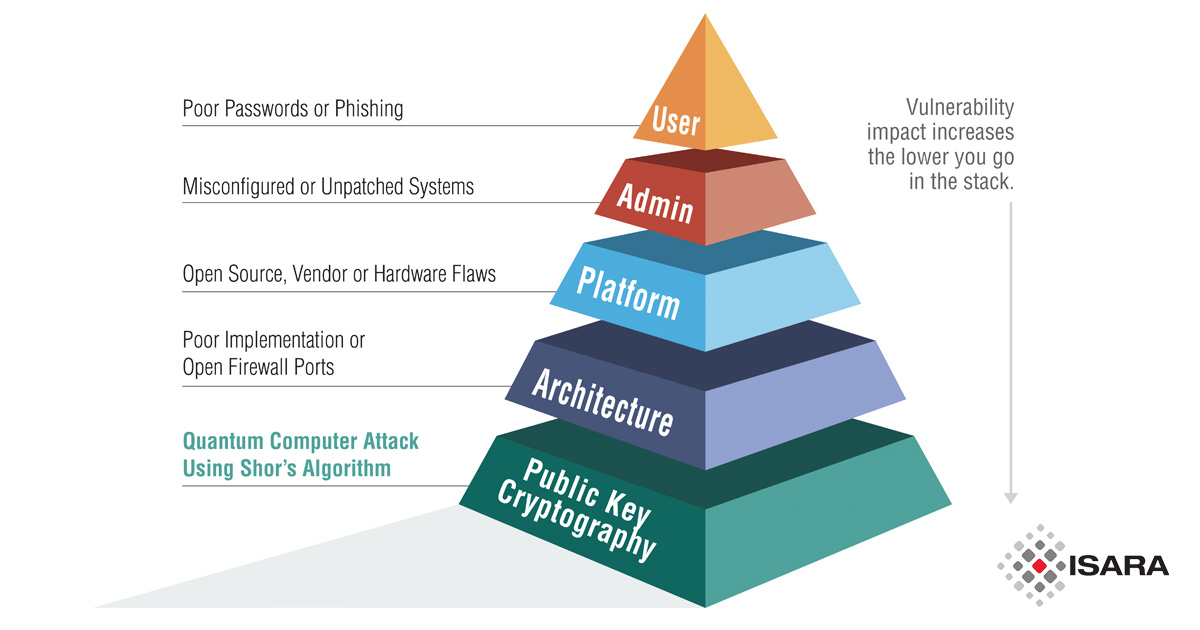
This could wreak havoc on our trust infrastructures in every industry and sector, including government, military, energy, aviation, financial services, automotive, and enterprise. Totzke recommends transitioning to quantum-safe security in three steps:
1. Inform your enterprise with Proof of Concept projects
2. Discover and enable crypto agility within existing infrastructure
3. Implement quantum-safe solutions
Preparing for quantum is no simple migration. In fact, the migration itself will take years of planning — especially for organizations with large and complex PKIs and mission-critical information, such as the U.S. Department of Defense. Bridging the gap between current and quantum-safe security — without affecting existing systems, adherence to standards, and end users — will require a new approach. The ISARA Catalyst Agile Digital Certificate Technology is a technique for creating an enhanced X.509 digital certificate that simultaneously contains two sets of cryptographic subject public keys and issuer signatures. This allows organizations to perform a gradual migration by upgrading their most critical, at-risk assets in phases.
NIST recommends that organizations:
- Develop a risk-based approach that takes into consideration security requirements, business operations, and mission impact
- Establish a communication plan to be used both within the organization and with external customers and partners
- Identify a migration timeline and the necessary resources
- Update or replace security standards, procedures, and recommended practice documentation
- Provide installation, configuration, and administration documentation
- Test and validate the new processes and procedures
“It is critical to begin planning for the replacement of hardware, software, and services that use public-key algorithms now so that the information is protected from future attacks,” urges NIST.