Introduction
The ISARA Radiate Security Solution Suite gives you the cryptographic building blocks to create applications that will resist attacks by quantum computers.
For more information about ISARA and our quantum safe solutions, please visit www.isara.com.
This Developer’s Guide tells you how to do things with the toolkit, such as:
-
use McEliece Quasi-Cyclic Moderate Density Parity-Check (QC-MDPC) error-correcting codes
-
use the Leighton-Micali Signature (LMS) scheme for digital signatures
-
use "NewHope" lattice based key agreement, or LUKE (Lattice based Unique Key Exchange), an ISARA speed-optimized variant
-
provide your own implementations of generic algorithms, such as hashes
The toolkit’s API is designed around generic algorithms; you create an instance
of the algorithm you want (say, SHA2-256) and then use it with the generic
algorithm APIs (iqr_HashBegin(), iqr_HashUpdate(), and iqr_HashEnd()).
Things like signature schemes and key agreement protocols are specialized enough to require customized APIs. We’ve designed these to follow the generic algorithm APIs as much as possible.
We recommend that you have an advanced understanding of cryptography and the theory of security protocols.
The Developer’s Guide covers the following topics:
-
Getting Started — Foundational information for using the toolkit.
-
FIPS 140-2 Certification — Using the FIPS 140-2 version of the toolkit
-
Hashing — How to use the toolkit’s BLAKE2b, SHA2, and SHA3 implementations, and how to provide your own implementations.
-
Random Numbers — How to generate pseudorandom bytes
-
Message Authentication Codes — How to use the HMAC and Poly1305 MACs.
-
Key Derivation Functions — How to use the KDFs
-
Symmetric Encryption — How to use the ChaCha20 symmetric-key encryption algorithm.
-
Digital Signatures — How to use the Dilithium, LMS, and Rainbow digital signature schemes.
-
Key Agreement — How to use the ECDH, LUKE, NewHope, and SIDH key agreement schemes.
-
Key Encapsulation — How to use the Kyber, McEliece, and NTRUPrime key encapsulation mechanisms.
-
Technical Info — Detailed information about the compiler options we’ve used, how to maximize code stripping when using the static toolkit, and other details that might be helpful.
-
Building On Windows — How to use the toolkit on the Windows platform.
Classical and Quantum Security
Cryptographic algorithms are often described as providing "x bits of security" when used with a certain set of parameters. These parameters can be tuned to provide additional security, usually at the cost of additional CPU and/or memory usage.
These x bits of security apply to an adversary equipped with classical, non- quantum computers, and will appear as "x bits of classical security" in the toolkit’s documentation. The strength of an algorithm against attacks by quantum computers will be "x bits of quantum security."
Some classes of algorithm, such as encryption schemes based on the discrete log problem, are thought to be easily breakable by adversaries equipped with quantum computers.
Some algorithms, such as cryptographic hashes and symmetric encryption schemes, are not known to be or believed to be efficiently breakable by a quantum adversary. Their quantum security strength is generally considered to be half of their classical strength. For example, SHA2-256 provides 256-bit classical security, and 128-bit quantum security.
Packaging
The toolkit ZIP archive contains the following files and directories:
-
README.html— Information about the toolkit package -
doc— API documentation and this Developer’s Guide -
include— toolkit headers -
lib_architecture— toolkit static and shared libraries for various CPU architectures -
samples— Sample programs demonstrating how to use the toolkit
Cryptographic signatures for the installation archives are distributed with the archives. If you don’t have access to the signatures, please contact support@isara.com.
Getting Help
The latest version of the toolkit documentation is available on the ISARA website. You can also request support via email.
-
1-800-319-8576 Toll-free (please refer to your support contract)
Samples
The samples directory has a number of sub-directories, each with a
self-contained program inside demonstrating how to use the toolkit for a
specific purpose:
-
aead_chacha20_poly1305andaead_chacha2_poly1305— Encrypt/decrypt using ChaCha20/Poly1305 for authenticated encryption. -
chacha20— Encrypt/decrypt using ChaCha20. -
dilithium— Generate Dilithium keys, sign a file’s data with a Dilithium key, and verify a Dilithium signature. -
ecdh— Perform an Elliptic-Curve Diffie-Hellman key exchange. -
hash— Hash a file’s data using BLAKE2b-256, BLAKE2b-512, SHA2-256, SHA2-512, SHA3-256, or SHA3-512. -
hmac— Get the HMAC tag for a file’s data using any of the available hash algorithms. -
kdf_concatenation,kdf_pbkdf2, andkdf_rfc5869— Derive a key (some pseudorandom data) using the specified key derivation function. -
kyber— Generate keys, encapsulate and decapsulate data using Kyber. -
lms— Generate keys, sign a file’s data, and verify a signature using the LMS algorithm. -
luke— Agree on a shared secret using the LUKE variant of the NewHope scheme. -
mceliece— Generate keys, encapsulate and decapsulate data using McEliece QC-MDPC. -
newhope— Agree on a shared secret using the NewHope scheme. -
ntruprime— Generate keys, encapsulate and decapsulate data using NTRUPrime. -
poly1305— Get the Poly1305 tag for a file’s data. -
rainbow— Generate keys, sign a file’s data, and verify a signature using the Rainbow algorithm. -
rng— Generate pseudorandom bytes using HMAC-DRBG or SHAKE. -
sidh— Agree on a shared secret using Supersingular Isogeny Diffie-Hellman.
To compile the samples, you will need:
-
C99 compliant compiler; recent versions of
clangorgccare preferred -
cmake3.7 or newer -
GNU
make3.8 or newer
Set your IQR_TOOLKIT_ROOT environment variable to the directory where you
unpacked the installation archive. The build will expect to find include and
lib inside the IQR_TOOLKIT_ROOT directory.
Compile all of the samples with:
-
cdto thesampledirectory. -
mkdir build -
cdto thebuilddirectory. -
cmake .. -
make
Getting Started
This section gives you an overview of things you’ll need to know to effectively use the toolkit.
Objects in the toolkit follow a standard cycle:
-
Create object.
-
Do things with the object.
-
Destroy the object.
Some things, like hashes, use a generic API; all hashes use the same Begin(),
Update(), End() functions.
Even algorithms that don’t use a generic API will have functions that indicate
exactly what they do. For example, LMS (a digital signature system) has
Sign() and Verify(), while McEliece QC-MDPC (a key encapsulation scheme) has
Encapsulate() and Decapsulate().
The Context
To create objects and algorithms in the toolkit, you need a Context. The
iqr_Context object keeps track of the registered hashing algorithms
as well as additional internal information.
One Context object can be used to create as many other toolkit objects as necessary. Use multiple Context objects if you need to provide several different hash implementations (for example).
The iqr_Context object and its APIs are defined in the iqr_context.h
header file. To create one:
#include "iqr_context.h"
...
iqr_Context *context = NULL;
iqr_retval result = iqr_CreateContext(&context);
if (result != IQR_OK) {
// Examine "result" to see what error has occurred.
}The toolkit’s Create() functions all take a Context as their first argument.
To properly destroy the context:
#include "iqr_context.h"
...
// Create an iqr_Context object.
// Do crypto.
...
iqr_retval result = iqr_DestroyContext(&context);
if (result != IQR_OK) {
// Examine "result" to see what error has occurred.
}Standardized Return Values
All of the APIs in the toolkit return an iqr_retval value, as defined in
the iqr_retval.h header.
On success, functions return IQR_OK; if an error occurs, the return value
will tell you why the error happened.
Use the iqr_StrError() function (also in iqr_retval.h) to convert an
iqr_retval value into an English string. Be sure to write your own error
messages if you need to support localization.
|
Note
|
Depending on your compiler flags, you must check the return values for toolkit functions. |
Registering Hashes
Many algorithms require hash implementations. The Context supplies these, but doesn’t provide a default implementation. This reduces the size of the code in your application by only linking in the algorithms you actually need to use. It also lets you provide your own implementations for additional speed or security.
See the iqr_HashRegisterCallbacks() function in iqr_hash.h.
The toolkit provides implementations of the quantum-safe BLAKE2b, SHA2 and SHA3 hash algorithms:
-
IQR_HASH_DEFAULT_BLAKE2B_256- C implementation of BLAKE2b-256 -
IQR_HASH_DEFAULT_BLAKE2B_512- C implementation of BLAKE2b-512 -
IQR_HASH_DEFAULT_SHA2_256- C implementation of SHA2-256 -
IQR_HASH_DEFAULT_SHA2_512- C implementation of SHA2-512 -
IQR_HASH_DEFAULT_SHA3_256- C implementation of SHA3-256 -
IQR_HASH_DEFAULT_SHA3_512- C implementation of SHA3-512
For example, to use the toolkit implementation of SHA2-256:
#include "iqr_context.h"
#include "iqr_hash.h"
...
// Create an iqr_Context object.
...
iqr_retval result = iqr_HashRegisterCallbacks(context, IQR_HASHALGO_SHA2_256,
&IQR_HASH_DEFAULT_SHA2_256);
if (result != IQR_OK) {
// Examine "result" to see what error has occurred.
}After this call to iqr_HashRegisterCallbacks() any toolkit APIs that need a
SHA2-256 object will create one using the toolkit’s built-in SHA2-256
implementation.
Thread Safety
Objects in the toolkit are self-contained. Any data required to use the object is controlled by the toolkit.
Access to the object is not managed by the toolkit. To use toolkit objects in a multi-threaded environment you’ll have to use the operating system’s mutexes or critical section guards carefully. Your use of the toolkit is as thread-safe as you make it so the toolkit can be as fast as possible in a single-threaded environment.
There are no global variables in the toolkit. There are no data structures with
shared, static data.
Anything that can be accessed from several threads needs to be locked in a way
that makes sense for the object. For example, with a hash, you’d need to wrap
the entire iqr_HashBegin()/iqr_HashUpdate()/iqr_HashEnd() sequence (or
the call to iqr_HashMessage()). For an RNG you might only need to
lock iqr_RNGGetBytes() calls (but that’d get more complex if you’re using one
that needs to be reseeded regularly).
Data Hygiene
Parameter objects (iqr_*Params) in the toolkit never contain any
cryptographic material.
All objects in the toolkit have their buffers wiped with 0x00 bytes prior
to being deallocated.
Buffers (seed data, hash inputs, etc.) passed to toolkit functions are never modified by the toolkit unless explicitly stated in API documentation.
What Next?
These sections can be read in any order, depending on what you need to do:
-
To hash some data into a digest, see Hashing.
-
To generate random bytes, see Random Numbers.
-
To create message authentication codes from data, see MACs.
-
To derive secret key data, see KDFs.
-
To perform symmetric encryption using a shared secret, see Symmetric Encryption.
-
To digitally sign and verify messages, see Digital Signatures.
-
To securely agree on a shared secret, see Key Agreement.
-
To generate a shared secret and encapsulate it for secure transport, see Key Encapsulation.
-
For detailed technical information about how the library was compiled, see Technical Info.
-
For information about building toolkit projects with Visual Studio, see Building on Windows.
FIPS 140-2 Certification
|
Note
|
If you’re not using the FIPS 140-2 certified version of the toolkit, you can
skip this section. Check your toolkit distribution files, or use
iqr_FIPS140GetState() to find out if you’ve got the FIPS 140-2 version.
|
The toolkit is being certified for Level 1 of FIPS 140-2 Security Requirements for Cryptographic Modules. If your toolkit has been compiled with FIPS 140-2 support, two modes are available:
-
IQR_FIPS140_DISABLED -
IQR_FIPS140_ENABLED
FIPS 140-2 mode applies to these algorithms:
-
SHA2-256, SHA2-512, SHA3-256, and SHA3-512
-
SHAKE-128, and SHAKE-256
-
HMAC with SHA2-256, SHA2-512, SHA3-256, or SHA3-512
-
HMAC-DRBG with SHA2-256, SHA2-512, SHA3-256, or SHA3-512
-
ECDH with the NIST-P256, NIST-P384, and NIST-P521 curves
The IQR_FIPS140_ENABLED mode adds some additional behaviour to the toolkit:
-
On library load, a code integrity test and various operational tests are performed. These tests are also performed when switching from
IQR_FIPS140_DISABLEDtoIQR_FIPS140_ENABLED. If any of these tests fail, onlyIQR_FIPS140_DISABLEDmode is available. -
ECDH key pairs will perform a self test during generation.
-
ECDH keys generated in FIPS 140-2 mode cannot be used when FIPS 140-2 mode is disabled. ECDH keys generated when FIPS 140-2 mode is disabled cannot be used when in FIPS 140-2 mode. Imported keys are not subject to this restriction (they could have come from anywhere), so be careful handling keys if you require ECDH in FIPS 140-2 mode.
Compiling With FIPS 140-2 Mode
To compile code with a FIPS 140-2 version of the toolkit, you must:
-
-DFIPS140=enabled -
Link against a FIPS 140-2 version of the library. These are provided as shared libraries only, as static libraries cannot automatically perform the required self tests on application start up.
Using FIPS 140-2 Mode
Use iqr_FIPS140GetState() and iqr_FIPS140SetState() (from iqr_fips140.h)
to get and set the FIPS 140-2 mode of the library.
The default state for a FIPS 140-2 version of the library is
IQR_FIPS140_ENABLED.
Approved RNG On-Demand Test
If you need to perform Approved RNG known-answer tests on-demand, use
iqr_FIPS140RNGTest() to trigger them (see iqr_fips140.h).
Hashing
Getting a hash digest for a message is a basic building block of many cryptographic algorithms. The toolkit provides implementations of BLAKE2b, SHA2 and SHA3.
Registering Hashes
As mentioned in the Getting Started section, you must register an implementation. The toolkit doesn’t automatically associate its own hashes with the Context when you create one.
#include "iqr_context.h"
#include "iqr_hash.h"
...
// Create iqr_Context.
...
iqr_retval result = iqr_HashRegisterCallbacks(context, algorithm,
implementation);The toolkit supports the following algorithms and provides the given implementations:
-
BLAKE2b-256 (
IQR_HASHALGO_BLAKE2B_256) —IQR_HASH_DEFAULT_BLAKE2B_256 -
BLAKE2b-512 (
IQR_HASHALGO_BLAKE2B_512) —IQR_HASH_DEFAULT_BLAKE2B_512 -
SHA2-256 (
IQR_HASHALGO_SHA2_256) —IQR_HASH_DEFAULT_SHA2_256 -
SHA2-512 (
IQR_HASHALGO_SHA2_512) —IQR_HASH_DEFAULT_SHA2_512 -
SHA3-256 (
IQR_HASHALGO_SHA3_256) —IQR_HASH_DEFAULT_SHA3_256 -
SHA3-512 (
IQR_HASHALGO_SHA3_512) —IQR_HASH_DEFAULT_SHA3_512
For example, to use the toolkit’s SHA3-512 implementation as the default for all SHA3-512 hashing:
#include "iqr_hash.h"
...
// Create iqr_Context.
...
iqr_retval result = iqr_HashRegisterCallbacks(context, IQR_HASHALGO_SHA3_512,
&IQR_HASH_DEFAULT_SHA3_512);|
Note
|
The iqr_Context object tracks all six of the supported BLAKE2b, SHA2, and SHA3
algorithms; you can register implementations for all of them on a single
iqr_Context.
|
Using Hashes
After an appropriate hash has been registered, you can use it with the generic hashing API. This API is the same for all hashes.
To create a hash object:
#include "iqr_hash.h"
...
// Create iqr_Context.
// Register hash implementations.
...
iqr_Hash *hash = NULL;
iqr_retval result = iqr_HashCreate(context, algorithm, &hash);
if (result != IQR_OK) {
// Handle error.
}To use a hash object:
...
// Call Begin() to initialize the hash.
result = iqr_HashBegin(hash);
if (result != IQR_OK) {
// Handle error.
}
// Call Update() zero or more times to add data to the hash.
result = iqr_HashUpdate(hash, buffer, buffer_size);
if (result != IQR_OK) {
// Handle error.
}
// Use iqr_HashGetDigestSize() to get the digest size for this hash.
uint8_t *digest = NULL;
size_t digest_size = 0;
result = iqr_HashGetDigestSize(hash, &digest_size);
if (result != IQR_OK) {
// Handle error.
}
digest = calloc(1, digest_size);
if (digest == NULL) {
// Handle out-of-memory.
}
// Call End() to finish the operation and get the digest.
result = iqr_HashEnd(hash, digest, digest_size);To destroy a hash object:
...
result = iqr_HashDestroy(&hash);
if (result != IQR_OK) {
// Handle error.
}There’s also an iqr_HashMessage() function that combines the
iqr_HashBegin(), iqr_HashUpdate(), and iqr_HashEnd() process into one
call:
...
result = iqr_HashMessage(hash, buffer, buffer_size, digest, digest_size);
if (result != IQR_OK) {
// Handle error.
}Randomized Hashing
The toolkit lets you use the randomized hashing algorithm described in
Strengthening
Digital Signatures via Randomized Hashing (by Shai Halevi and Hugo Krawczyk)
by adding salt to your iqr_Hash object.
|
Note
|
The Randomized Hashing algorithm only supports Merkle-Damgård hashes, such as BLAKE2b and SHA2. You cannot use it with SHA3. |
The salt data is added to the hash’s state whenever additional data is added to the hash. The salt data must be at least 16 bytes, and will be expanded or truncated to match the hash’s block length.
To add salt to your hash object:
#include "iqr_hash.h"
...
// Create iqr_Context.
// Register hash implementations.
...
iqr_Hash *hash = NULL;
iqr_retval result = iqr_HashCreate(context, algorithm, &hash);
if (result != IQR_OK) {
// Handle error.
}
result = iqr_HashSetSalt(hash, salt_buffer, salt_buffer_size);
if (result != IQR_OK) {
// Handle error.
}You can call iqr_HashSetSalt() before iqr_HashBegin() or after
iqr_HashEnd(), and the salt data is applied to all hashing operations
performed using the same iqr_Hash object.
Because the salt can be expanded or truncated, you can use
iqr_HashGetSaltSize() and iqr_HashGetSalt() to retrieve the modified salt
data:
...
size_t salt_size = 0;
result = iqr_HashGetSaltSize(hash, &salt_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *salt_data = calloc(1, salt_size);
if (salt_data == NULL) {
// Handle error.
}
result = iqr_HashGetSalt(hash, salt_data, salt_size);
if (result != IQR_OK) {
// Handle error.
}Writing a Hash Implementation
Because the toolkit doesn’t have a default hash implementation associated with
the iqr_Context object, you can use the iqr_HashCallbacks structure (from
iqr_hash.h) to provide your own code. This is handy if you have hardware
that provides fast hashing, or you want to use another library’s implementation.
The iqr_HashCallbacks structure shows you the signatures of the functions
you’ll need to implement:
typedef struct {
iqr_retval (*initialize)(void **state);
iqr_retval (*begin)(void *state);
iqr_retval (*update)(void *state, const uint8_t *data, size_t size);
iqr_retval (*end)(void *state, uint8_t *digest, size_t size);
iqr_retval (*cleanup)(void **state);
} iqr_HashCallbacks;The initialize() function is passed an empty pointer, where you can store
any necessary state. Allocate any memory you need.
#include "iqr_hash.h"
#include "iqr_retval.h"
...
iqr_retval myhash_initialize(void **state)
{
// Sanity-check inputs.
if (state == NULL) {
return IQR_ENULLPTR;
}
if (*state != NULL) {
return IQR_EINVPTR;
}
// Allocate whatever state you need. It's OK to leave it
// NULL if you don't need to track any state.
myhash_state *myhash = calloc(1, sizeof(myhash_state));
if (myhash == NULL) {
return IQR_ENOMEM;
}
...
*state = myhash;
return IQR_OK;
}Your begin() function is called at the start of a new hashing operation.
Initialize your hash code, and get ready to accept data.
#include "iqr_hash.h"
#include "iqr_retval.h"
...
iqr_retval myhash_begin(void *state)
{
// Sanity-check inputs.
if (state == NULL) {
return IQR_ENULLPTR;
}
// Perform any other pre-hashing initialization.
...
return IQR_OK;
}The update() function is passed the state pointer, a buffer, and the size of
the buffer in bytes. Add the buffer’s data to your hash state. This function
can be called zero or more times during a hashing operation.
iqr_retval myhash_update(void *state, uint8_t *data, size_t data_size)
{
// Sanity-check input.
if (data == NULL && data_size != 0) {
return IQR_ENULLPTR;
}
if (data_size == 0) {
return IQR_OK;
}
// Add the data from the buffer to your hash.
...
return IQR_OK;
}The end() function gets the state pointer, a buffer, and the size of the
buffer in bytes. Complete the hashing operation and store its digest in the
supplied buffer.
iqr_retval myhash_end(void *state, uint8_t *digest, size_t digest_size)
{
// Sanity-check input.
if (state == NULL || digest == NULL) {
return IQR_ENULLPTR;
}
// Make sure there's enough room to store your digest.
if (digest_size != MYHASH_DIGEST_SIZE) {
return IQR_EINVBUFSIZE;
}
// Finish processing the hash.
...
// Extract the digest and store it in the given buffer.
...
}Finally, the cleanup() function gets a pointer to the state pointer. Wipe and
deallocate any state you allocated during initialize() and set the state
pointer to NULL.
iqr_retval myhash_cleanup(void **state)
{
// Clean up and deallocate any state you allocated.
...
memset(*state, 0, sizeof(myhash_state));
free(*state);
*state = NULL;
return IQR_OK;
}|
Note
|
The end() function is always called when a hash object is destroyed,
whether or not begin() and update() succeeded.
|
Using OpenSSL’s SHA2-256
For a concrete example of creating your own hash implementation, let’s use OpenSSL’s SHA2-256.
First, we’ll write the hash’s initialize(), begin(), update(), end(),
and cleanup() functions using calls to the OpenSSL library:
#include "iqr_hash.h"
#include "iqr_retval.h"
#include <openssl/sha.h>
// OpenSSL APIs return 1 for success.
#define OPENSSL_OK 1
static iqr_retval sha2_256_initialize(void **state)
{
// Sanity-check inputs.
if (state == NULL) {
return IQR_ENULLPTR;
}
if (*state != NULL) {
return IQR_EINVPTR;
}
// Allocate an OpenSSL SHA256_CTX to store the state.
SHA256_CTX *ctx = NULL;
ctx = calloc(1, sizeof(*ctx));
if (ctx == NULL) {
return IQR_ENOMEM;
}
*state = ctx;
return IQR_OK;
}
static iqr_retval sha2_256_begin(void *state)
{
// Sanity-check inputs.
if (state == NULL) {
return IQR_ENULLPTR;
}
SHA256_CTX *ctx = (SHA256_CTX *)state;
// Let OpenSSL set up its context.
int rc = SHA256_Init(ctx);
if (rc != OPENSSL_OK) {
return IQR_ENOTINIT;
}
return IQR_OK;
}
static iqr_retval sha2_256_update(void *state, const uint8_t *data,
size_t size)
{
// Sanity-check input.
if (data == NULL && data_size != 0) {
return IQR_ENULLPTR;
}
if (data_size == 0) {
return IQR_OK;
}
// In this case, the state can't be NULL.
if (state == NULL) {
return IQR_ENULLPTR;
}
SHA256_CTX *ctx = (SHA256_CTX *)state;
// Pass the data pointer into the OpenSSL update function.
int rc = SHA256_Update(ctx, data, size);
if (rc != OPENSSL_OK) {
// Update failed.
return IQR_EINVOBJECT;
}
return IQR_OK;
}
static iqr_retval sha2_256_end(void *state, uint8_t *digest, size_t digest_size)
{
// Sanity-check input.
if (state == NULL || digest == NULL) {
return IQR_ENULLPTR;
}
SHA256_CTX *ctx = (SHA256_CTX *)state;
// Make sure there's enough room to store your digest.
if (digest_size != IQR_SHA2_256_DIGEST_SIZE) {
return IQR_EINVBUFSIZE;
}
// Pass the data pointer into the OpenSSL Final function.
int rc = SHA256_Final(digest, *ctx);
if (rc != OPENSSL_OK) {
return IQR_EINVOBJECT;
}
return IQR_OK;
}
static iqr_retval sha2_256_cleanup(void **state)
{
SHA256_CTX *ctx = (SHA256_CTX *)*state;
memset(ctx, 0, sizeof(*ctx));
free(ctx);
*state = NULL;
return IQR_OK;
}Now that we’ve got an implementation, we need to register it so the rest of the toolkit can use it when an algorithm needs a SHA2-256 hash:
// Create the callback structure.
const iqr_HashCallbacks openssl_sha2_256 = {
.initialize = sha2_256_initialize,
.begin = sha2_256_begin,
.update = sha2_256_update,
.end = sha2_256_end,
.cleanup = sha2_256_cleanup
};
// Register the OpenSSL implementation.
result = iqr_HashRegisterCallbacks(context, IQR_HASHALGO_SHA2_256,
&openssl_sha2_256);
if (result != IQR_OK) {
// Handle error.
}After that, any IQR_HASHALGO_SHA2_256 hash object you create with that
iqr_Context object will use the OpenSSL implementation:
iqr_Hash *hash = NULL;
iqr_retval result = iqr_HashCreate(context, IQR_HASHALGO_SHA2_256, &hash);
if (result != IQR_OK) {
// Handle error.
}Using Microsoft’s SHA2-256
Windows Vista and newer operating systems feature Microsoft’s Cryptography API: Next Generation (CNG). This example demonstrates a SHA2-256 implementation that wraps Microsoft’s CNG functions. For more information, see the Creating a Reusable Hashing Object documentation.
The Windows API can return a number of error codes. In this example, we ignore
the NTSTATUS codes and replace them with out own iqr_retval codes. You must
handle NTSTATUS codes appropriately for your application.
First, we’ll write the hash’s initialize(), begin(), update(), end(),
and cleanup() functions:
#ifndef WIN32_LEAN_AND_MEAN
#define WIN32_LEAN_AND_MEAN // Exclude rarely-used stuff from Windows headers.
#endif
#include <windows.h>
#include <bcrypt.h>
#include <ntstatus.h>
// This used to be in <ntstatus.h>, but was removed in recent versions of the
// Platform SDK.
#ifndef NT_SUCCESS
#define NT_SUCCESS(status) (status >= 0)
#endif
#include "iqr_hash.h"
#include "iqr_retval.h"
// This will be our state.
typedef struct {
BCRYPT_ALG_HANDLE alg;
BCRYPT_HASH_HANDLE hash;
} BCRYPT_HANDLES;
static iqr_retval cng_sha2_256_initialize(void **state)
{
// Sanity-check inputs.
if (state == NULL) {
return IQR_ENULLPTR;
}
if (*state != NULL) {
return IQR_EINVPTR;
}
BCRYPT_HANDLES *handles = NULL;
// Allocate the state that will be passed around.
handles = calloc(1, sizeof(BCRYPT_HANDLES));
if (handles == NULL) {
return IQR_ENOMEM;
}
// A reusable hash object will automatically reset for reuse following a
// call to BCryptFinishHash(). Thus it is not necessary to recreate a
// hashing handle.
DWORD flag = BCRYPT_HASH_REUSABLE_FLAG;
NTSTATUS status = BCryptOpenAlgorithmProvider(&handles->alg,
BCRYPT_SHA256_ALGORITHM, NULL, flag);
if (NT_SUCCESS(status) == false) {
goto cleanup;
}
status = BCryptCreateHash(handles->alg, &handles->hash, NULL, 0, NULL, 0, flag);
if (NT_ERROR(status)) {
goto cleanup;
}
// Success! Set the state and exit.
*state = handles;
return IQR_OK;
cleanup:
BCryptCloseAlgorithmProvider(handles->alg, 0);
free(handles);
return IQR_ENOTINIT;
}
static iqr_retval cng_sha2_256_begin(void *state)
{
// A reusable hash object automatically resets its internal state.
//
// By reusing a hash object, this implementation favours speed by
// utilizing more memory. An alternative implementation could call
// BCryptCreateHash() here without the use of BCRYPT_HASH_REUSABLE_FLAG.
return IQR_OK;
}
static iqr_retval cng_sha2_256_update(void *state, const uint8_t *data,
size_t size)
{
// Sanity-check input.
if (data == NULL && data_size != 0) {
return IQR_ENULLPTR;
}
if (data_size == 0) {
return IQR_OK;
}
// In this case, the state can't be NULL.
if (state == NULL) {
return IQR_ENULLPTR;
}
BCRYPT_HANDLES *handles = state;
NTSTATUS status = BCryptHashData(handles->hash, (PUCHAR)data, (ULONG)size, 0);
if (NT_SUCCESS(status) == false) {
return IQR_EINVOBJECT;
}
return IQR_OK;
}
static iqr_retval cng_sha2_256_end(void *state, uint8_t *digest, size_t digest_size)
{
// Sanity-check input.
if (state == NULL || digest == NULL) {
return IQR_ENULLPTR;
}
// Make sure there's enough room to store your digest.
if (digest_size != IQR_SHA2_256_DIGEST_SIZE) {
return IQR_EINVBUFSIZE;
}
BCRYPT_HANDLES *handles = state;
// The hash object automatically resets once this call succeeds.
NTSTATUS status = BCryptFinishHash(handles->hash, (PUCHAR)digest, (ULONG)size, 0);
if (NT_SUCCESS(status) == false) {
return IQR_EINVOBJECT;
}
return IQR_OK;
}
static iqr_retval cng_sha2_256_cleanup(void **state)
{
// Sanity-check input.
if (state == NULL) {
return IQR_ENULLPTR;
}
BCRYPT_HANDLES *handles = *state;
NTSTATUS status = BCryptDestroyHash(handles->hash);
if (NT_SUCCESS(status) == false) {
return IQR_EINVOBJECT;
}
status = BCryptCloseAlgorithmProvider(handles->alg, 0);
if (NT_SUCCESS(status) == false) {
return IQR_EINVOBJECT;
}
memset(handles, 0, sizeof(*handles));
free(handles);
*state = NULL;
return IQR_OK;
}Now we use iqr_HashRegisterCallbacks() to register this implementation as
the SHA2-256 hash:
// Create the callback structure.
const iqr_HashCallbacks cng_sha2_256 = {
.initialize = cng_sha2_256_initialize,
.begin = cng_sha2_256_begin,
.update = cng_sha2_256_update,
.end = cng_sha2_256_end,
.cleanup = cng_sha2_256_cleanup
};
// Register the CNG implementation.
result = iqr_HashRegisterCallbacks(context, IQR_HASHALGO_SHA2_256,
&cng_sha2_256);
if (result != IQR_OK) {
// Handle error.
}Now, any IQR_HASHALGO_SHA2_256 hash object you create will use the
CNG SHA2-2 256 implementation:
iqr_Hash *hash = NULL;
iqr_retval result = iqr_HashCreate(context, IQR_HASHALGO_SHA2_256, &hash);
if (result != IQR_OK) {
// Handle error.
}Random Numbers
Generating random data is an important part of many cryptographic algorithms. The toolkit supports the HMAC-DRBG and SHAKE algorithms for generating data.
For simplicity, we refer to this class of algorithm as random number generators (RNGs).
Seed Data
Pseudo-random number generators are only as good as the seed data you use to initialize them. This seed data must come from a good source of entropy.
Refer to your target system’s CPU or OS documentation to find the best source of entropy available to you.
Using a poor source of entropy data will compromise the randomness of the data produced by these algorithms.
Using RNGs
Like hashes, RNGs use a generic API. Unlike hashes, the RNGs
supported by the toolkit require custom Create() functions to provide
suitable initialization data for each algorithm.
To create an HMAC-DRBG object using any of the IQR_HASHALGO_* constants
from iqr_hash.h:
#include "iqr_context.h"
#include "iqr_hash.h"
#include "iqr_rng.h"
...
// Create iqr_Context.
// Register a hash implementation for the implementation you want to use
// (IQR_HASHALGO_SHA2_256 in this example).
...
iqr_RNG *rng = NULL;
iqr_retval result = iqr_RNGCreateHMACDRBG(context, IQR_HASHALGO_SHA2_256, &rng);
if (result != IQR_OK) {
// Handle error.
}|
Note
|
To provide a nonce for HMAC-DRBG, include it in the seed data given to
iqr_RNGInitialize(). If your seed data was "password" and your nonce is
"random", set the initialization buffer to "passwordrandom".
|
To create a SHAKE object using any of the IQR_SHAKE_* constants from
iqr_rng.h:
#include "iqr_context.h"
#include "iqr_rng.h"
...
// Create iqr_Context.
...
iqr_RNG *rng = NULL;
iqr_retval result = iqr_RNGCreateSHAKE(context, IQR_SHAKE_256_SIZE, &rng);
if (result != IQR_OK) {
// Handle error.
}To create an RNG object using your own implementation:
#include "iqr_context.h"
#include "iqr_rng.h"
...
// Create iqr_Context.
...
iqr_RNGCallbacks rng_callbacks = {
.initialize = my_rng_initialize,
.reseed = my_rng_reseed,
.getbytes = my_rng_getbytes,
.cleanup = my_rng_cleanup
};
...
iqr_RNG *rng = NULL;
iqr_retval result = iqr_RNGCreate(context, &rng_callbacks, &rng);
if (result != IQR_OK) {
// Handle error.
}To use an RNG object:
...
// Call Initialize() to initialize the RNG.
result = iqr_RNGInitialize(rng, seed_buffer, seed_size);
if (result != IQR_OK) {
// Handle error.
}
// Call GetBytes() to get bytes from the RNG.
result = iqr_RNGGetBytes(rng, buffer, buffer_size);
if (result == IQR_ERESEED) {
// The RNG is depleted, call Reseed() to give it more seed data.
result = iqr_RNGReseed(rng, new_seed_buffer, new_seed_size);
if (result != IQR_OK) {
// Handle error.
}
result = iqr_RNGGetBytes(rng, buffer, buffer_size);
if (result != IQR_OK) {
// Handle error.
}
} else if (result != IQR_OK) {
// Handle error.
}
// You can also reseed the RNG as necessary; you don't
// need to wait until GetBytes() returns IQR_ERESEED.
result = iqr_RNGReseed(rng, new_seed_buffer, new_seed_size);
if (result != IQR_OK) {
// Handle error.
}To destroy an RNG object:
...
result = iqr_RNGDestroy(&rng);
if (result != IQR_OK) {
// Handle error.
}Writing an RNG Implementation
Because the toolkit doesn’t have a default RNG implementation, you can use the
iqr_RNGCallbacks structure (from iqr_rng.h) to provide your own code. This
is handy if you have hardware that provides cryptographically secure random
number generation, or you want to use another library’s implementation.
The iqr_RNGCallbacks structure shows you the signatures of the functions
you’ll need to implement:
typedef struct {
iqr_retval (*initialize)(void **state, const uint8_t *seed,
size_t seed_size);
iqr_retval (*reseed)(void *state, const uint8_t *entropy,
size_t entropy_size);
iqr_retval (*getbytes)(void *state, uint8_t *buffer, size_t buffer_size);
iqr_retval (*cleanup)(void **state);
} iqr_RNGCallbacks;Your initialize() function is passed an empty pointer, which it can use to
store any necessary state. In addition, you’re passed a buffer containing seed
data, and the size (in bytes) of that buffer. Allocate any memory you need,
initialize your RNG code, and get ready to generate bytes.
#include "iqr_retval.h"
#include "iqr_rng.h"
...
iqr_retval myrng_initialize(void **state, const uint8_t *seed, size_t seed_size)
{
// Sanity-check inputs.
if (state == NULL || seed == NULL) {
return IQR_ENULLPTR;
}
if (*state != NULL) {
return IQR_EINVPTR;
}
// The caller must provide seed data.
if (seed_size == 0) {
return IQR_EINVBUFSIZE;
}
// Allocate whatever state you need. It's OK to leave it
// NULL if you don't need to track any state.
myrng_state *myrng = calloc(1, sizeof(myrng_state));
if (myrng == NULL) {
return IQR_ENOMEM;
}
...
*state = myrng;
// Perform any other initialization.
...
return IQR_OK;
}The reseed() function is passed the state pointer, a buffer, and the size of
the buffer in bytes. Add the buffer’s data to your RNG’s internal entropy.
iqr_retval myrng_reseed(void *state, uint8_t *seed, size_t seed_size)
{
// Sanity-check input.
if (seed == NULL) {
return IQR_ENULLPTR;
}
if (seed_size == 0) {
return IQR_EINVBUFSIZE;
}
// Add the data from the seed to your RNG's entropy.
...
return IQR_OK;
}The getbytes() function is passed the state pointer, a buffer, and the size
of the buffer in bytes. Write that many random bytes into the buffer.
iqr_retval myrng_getbytes(void *state, uint8_t *buffer, size_t buffer_size)
{
// Sanity-check input.
if (buffer == NULL) {
return IQR_ENULLPTR;
}
if (buffer_size == 0) {
return IQR_EINVBUFSIZE;
}
// Generate random bytes and write them into the buffer.
...
return IQR_OK;
}Finally, the cleanup() function gets a pointer to the state pointer. Before
returning, deallocate any state you allocated during initialize() and set the
state pointer to NULL.
iqr_retval myrng_cleanup(void **state)
{
// Sanity-check input.
if (state == NULL) {
return IQR_ENULLPTR;
}
// Clean up and deallocate any state you allocated.
...
memset(*state, 0, sizeof(myrng_state));
free(*state);
*state = NULL;
return IQR_OK;
}|
Note
|
The cleanup() function is always called when an RNG object is destroyed,
whether or not initialize(), getbytes(), and reseed() succeeded.
|
Using /dev/urandom as an RNG
Here’s a concrete example of how to create your own RNG implementation, using
/dev/urandom as a source of random bytes. Refer to your operating system’s
/dev/urandom documentation for details about its behaviour, and its
suitability as a cryptographic random number generator.
This sample assumes your /dev/urandom implementation lets you write additional
entropy to the device.
First, we’ll write the RNG’s initialize(), reseed(), getbytes(), and
cleanup() functions using POSIX functions and /dev/urandom:
#include <fcntl.h>
#include <stdint.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include "iqr_context.h"
#include "iqr_retval.h"
#include "iqr_rng.h"
static iqr_retval devrandom_initialize(void **state, const uint8_t *seed,
size_t seed_size)
{
// Sanity-check inputs.
if (state == NULL || seed == NULL) {
return IQR_ENULLPTR;
}
if (*state != NULL) {
return IQR_EINVPTR;
}
// The caller must provide seed data.
if (seed_size == 0) {
return IQR_EINVBUFSIZE;
}
int *device_handle = calloc(1, sizeof(int));
if (device_handle == NULL) {
return IQR_ENOMEM;
}
iqr_retval result = IQR_OK;
// Write our seed data to the device.
*device_handle = open("/dev/urandom", O_RDWR);
if (*device_handle == -1) {
result = IQR_ENOTINIT;
goto cleanup;
}
ssize_t bytes_written = 0;
while (seed_size > 0) {
bytes_written = write(*device_handle, seed, seed_size);
if (bytes_written == -1) {
result = IQR_EINVOBJECT;
goto cleanup;
}
seed_size -= (size_t)bytes_written;
}
// We don't need to allocate state, just store the file descriptor.
*state = device_handle;
return result;
cleanup:
if (*device_handle != -1) {
close(*device_handle);
free(device_handle);
device_handle = NULL;
}
return result;
}
static iqr_retval devrandom_reseed(void *state, const uint8_t *entropy,
size_t entropy_size)
{
// Sanity-check input.
if (state == NULL || entropy == NULL) {
return IQR_ENULLPTR;
}
if (entropy_size == 0) {
return IQR_EINVBUFSIZE;
}
// Add the data to your RNG's entropy.
int *device_handle = state;
ssize_t bytes_written = 0;
while (entropy_size > 0) {
bytes_written = write(*device_handle, entropy, entropy_size);
if (bytes_written == -1) {
return IQR_EINVOBJECT;
}
entropy_size -= (size_t)bytes_written;
}
return IQR_OK;
}
static iqr_retval devrandom_getbytes(void *state, uint8_t *buffer,
size_t buffer_size)
{
// Sanity-check input.
if (state == NULL || buffer == NULL) {
return IQR_ENULLPTR;
}
if (buffer_size == 0) {
return IQR_EINVBUFSIZE;
}
// Generate random bytes and write them into the buffer.
int *device_handle = state;
ssize_t bytes_read = 0;
while (buffer_size > 0) {
bytes_read = read(*device_handle, buffer + bytes_read, buffer_size);
if (bytes_read == -1) {
return IQR_EINVDATA;
}
buffer_size -= (size_t)bytes_read;
}
return IQR_OK;
}
static iqr_retval devrandom_cleanup(void **state)
{
// Sanity-check input.
if (state == NULL) {
return IQR_ENULLPTR;
}
// Clean up and deallocate any state you allocated.
int *device_handle = *state;
close(*device_handle);
free(device_handle);
*state = NULL;
return IQR_OK;
}Now that you’ve got an implementation, you can use it with iqr_RNGCreate():
// Create the callback structure.
static const iqr_RNGCallbacks devrandom_rng = {
.initialize = devrandom_initialize,
.reseed = devrandom_reseed,
.getbytes = devrandom_getbytes,
.cleanup = devrandom_cleanup
};
iqr_RNG *rng = NULL;
iqr_retval result = iqr_RNGCreate(context, &devrandom_rng, &rng);
if (result != IQR_OK) {
// Handle error.
}Using Microsoft’s Cryptographic Service as an RNG
Windows Vista and newer operating systems feature Microsoft’s Cryptography API: Next Generation (CNG). Like the previous example, the following code demonstrates an RNG implementation that wraps Microsoft’s random number generation functions. For more information, please see the CNG documentation.
Windows constantly adds entropy, so the CNG random number generator does not need to be reseeded.
The Windows API can return a number of error codes. In this example, we ignore
the NTSTATUS codes and replace them with our own iqr_retval codes. You
must handle NTSTATUS codes appropriately for your application.
First, we’ll write the RNG’s initialize(), reseed(), getbytes(), and
cleanup() functions:
#ifndef WIN32_LEAN_AND_MEAN
#define WIN32_LEAN_AND_MEAN // Exclude rarely-used stuff from Windows headers.
#endif
#include <windows.h>
#include <bcrypt.h>
#include <ntstatus.h>
// This may not exists in <ntstatus.h>
#ifndef NT_SUCCESS
#define NT_SUCCESS(status) (status >= 0)
#endif
#include "iqr_context.h"
#include "iqr_retval.h"
#include "iqr_rng.h"
static iqr_retval cng_rng_initialize(void **state, const uint8_t *seed,
size_t seed_size)
{
// Sanity-check inputs.
if (state == NULL || seed == NULL) {
return IQR_ENULLPTR;
}
if (*state != NULL) {
return IQR_EINVPTR;
}
BCRYPT_ALG_HANDLE alg = NULL;
// Open a handle to the CNG.
NTSTATUS status = BCryptOpenAlgorithmProvider(&alg, BCRYPT_RNG_ALGORITHM, NULL, 0);
if (NT_SUCCESS(status) == false) {
return IQR_ENOTINIT;
}
*state = alg;
return result;
}
static iqr_retval cng_rng_reseed(void *state, const uint8_t *entropy,
size_t entropy_size)
{
// The CNG random number generator will never need reseeding.
return IQR_OK;
}
static iqr_retval cng_rng_getbytes(void *state, uint8_t *buffer,
size_t buffer_size)
{
// Sanity-check input.
if (state == NULL || buffer == NULL) {
return IQR_ENULLPTR;
}
if (buffer_size == 0) {
return IQR_EINVBUFSIZE;
}
BCRYPT_ALG_HANDLE alg = state;
// Generate requested random bytes.
NTSTATUS status = BCryptGenRandom(alg, (PUCHAR)buffer, (ULONG)buffer_size, 0);
if (NT_SUCCESS(status) == false) {
return IQR_EINVOBJECT;
}
return IQR_OK;
}
static iqr_retval sng_rng_cleanup(void **state)
{
// Sanity-check input.
if (state == NULL) {
return IQR_ENULLPTR;
}
BCRYPT_ALG_HANDLE alg = *state;
// Close the provider handle.
NTSTATUS status = BCryptCloseAlgorithmProvider(alg, 0);
if (NT_SUCCESS(status) == false) {
return IQR_EINVOBJECT;
}
*state = NULL;
return IQR_OK;
}Once the implementation is finished, it’s ready to use with iqr_RNGCreate():
// Create the callback structure.
static const iqr_RNGCallbacks cng_rng = {
.initialize = cng_dev_initialize,
.reseed = cng_dev_reseed,
.getbytes = cng_dev_getbytes,
.cleanup = cng_dev_cleanup
};
iqr_RNG *rng = NULL;
iqr_retval result = iqr_RNGCreate(context, &cng_rng, &rng);
if (result != IQR_OK) {
// Handle error.
}Message Authentication Codes
The toolkit provides two message authentication code algorithms, HMAC and Poly1305.
MACs have the following key length requirements, based on the algorithm:
-
HMAC (SHA2-256 or SHA3-256) - 32 bytes or more
-
HMAC (SHA2-512 or SHA3-512) - 64 bytes or more
-
Poly1305 - 32 bytes (more is allowed, but additional data will be ignored)
Using MACs
Using a MAC is similar to using a hash:
-
Create the MAC using
iqr_MACCreateHMAC()oriqr_MACCreatePoly1305(). -
Begin the MAC operation.
-
Update it with data.
-
End the MAC and get the tag.
-
Destroy the MAC, or begin again.
The hash based message authentication code (HMAC) algorithm (found in
iqr_mac.h) requires you to register an implementation for the hashing
algorithm you want to use; see the hashing section for more
information about hash algorithms.
To create an HMAC:
#include "iqr_hash.h"
#include "iqr_mac.h"
...
// Create iqr_Context.
// Register hash implementations.
...
iqr_MAC *mac = NULL;
iqr_retval result = iqr_MACCreateHMAC(context, algorithm, &mac);
if (result != IQR_OK) {
// Handle error.
}The Poly1305 message authentication code algorithm (found in iqr_mac.h)
doesn’t have any external dependencies, but does require a one-time key. It can
be combined with the ChaCha20 cipher to provide
Authenticated Encryption with Associated Data (AEAD) as demonstrated in the
aead_chacha20_poly1305 sample
(in your samples directory, or
found on GitHub).
To create a Poly1305 MAC:
#include "iqr_mac.h"
...
// Create iqr_Context.
...
iqr_MAC *mac = NULL;
iqr_retval result = iqr_MACCreatePoly1305(context, &mac);
if (result != IQR_OK) {
// Handle error.
}To use a MAC object:
...
// Call Begin() to initialize the MAC.
result = iqr_MACBegin(mac, key, key_size);
if (result != IQR_OK) {
// Handle error.
}
// Call Update() zero or more times to add data to the MAC.
result = iqr_MACUpdate(mac, buffer, buffer_size);
if (result != IQR_OK) {
// Handle error.
}
// Use iqr_MACGetTagSize() to get the tag size for this MAC.
uint8_t *tag = NULL;
size_t tag_size = 0;
result = iqr_MACGetTagSize(mac, &tag_size);
if (result != IQR_OK) {
// Handle error.
}
tag = calloc(1, tag_size);
if (tag == NULL) {
// Handle out-of-memory.
}
// Call End() to finish the operation and get the tag.
result = iqr_MACEnd(mac, tag, tag_size);
if (result != IQR_OK) {
// Handle error.
}To destroy a MAC object:
...
result = iqr_MACDestroy(&mac);
if (result != IQR_OK) {
// Handle error.
}There’s also an iqr_MACMessage() function that combines the
iqr_MACBegin(), iqr_MACUpdate(), iqr_MACEnd() process into one call:
...
result = iqr_MACMessage(mac, key, key_size, buffer, buffer_size, tag, tag_size);
if (result != IQR_OK) {
// Handle error.
}Key Derivation Functions
The toolkit provides three standard key derivation functions (KDFs):
-
RFC-5869’s HMAC based extract-and-expand KDF (HKDF)
-
NIST SP 800-56A Alternative 1 Concatenation KDF
-
RFC-2898’s Password Based Key Derivation Function 2 (PBKDF2)
Because the KDFs all have slightly different needs, there is no generic KDF API.
|
Warning
|
The KDF APIs will change in the next version of the toolkit. For more information see Deprecated APIs. |
RFC-5869 HKDF
Because the RFC-5869 KDF uses an HMAC internally, you must register a hashing algorithm before using the KDF.
To use the RFC-5869 HMAC based KDF:
#include "iqr_context.h"
#include "iqr_hash.h"
#include "iqr_kdf.h"
...
// Create iqr_Context.
// Register hashing algorithms.
...
iqr_retval result = iqr_RFC5869HKDFDeriveKey(context, hash_algorithm,
salt_buffer, salt_size, ikm_buffer, ikm_size, info_buffer, info_size,
key_buffer, key_size);
if (result != IQR_OK) {
// Handle error.
}Use the salt buffer to provide additional randomness. The salt buffer can be
NULL (and the salt buffer size 0), but providing salt will improve the
security of your application.
The initial keying material (the IKM buffer) is similar to the seeding data given to a random number generator. Some algorithms may have an existing cryptographically strong key to use for the initial keying material, such as the premaster secret in TLS RSA cipher suites. You must provide data in this buffer.
The optional info buffer is for context and application specific information. This binds the derived key to your information, such as a protocol number, an algorithm identifier, user data, etc.
The derived key data is returned in the key buffer. The key size cannot be more
than 254 times the size of the hash’s digest size or this will return an
IQR_EOUTOFRANGE error.
|
Note
|
RFC-5869 HKDF is the cryptographically strongest KDF currently provided by the toolkit. |
NIST Concatenation KDF
Because the NIST SP 800-56A Alternative 1 Concatenation KDF uses a hash internally, you must register a hashing algorithm before using the KDF.
To use the Concatenation KDF:
#include "iqr_context.h"
#include "iqr_hash.h"
#include "iqr_kdf.h"
...
// Create iqr_Context.
// Register hashing algorithms.
...
iqr_retval result = iqr_ConcatenationKDFDeriveKey(context, hash_algorithm,
shared_secret, shared_secret_size, other_info, other_info_size,
key_buffer, key_size);
if (result != IQR_OK) {
// Handle error.
}The shared secret ("Z" in the specification) is pre-determined data shared between all systems generating keys with the Concatenation KDF. The shared secret must be at least one byte.
The other info ("OtherInfo" in the specification) is for context and
application specific information. This binds the derived key to your
information, such as a protocol number, an algorithm identifier, user data,
etc. It can be NULL (and set the buffer size to 0).
The derived key is returned in the key buffer.
RFC-2898 PBKDF2
Because the RFC-2898 PBKDF2 uses a hash internally, you must register a hashing algorithm before using the KDF.
To use PBKDF2:
#include "iqr_context.h"
#include "iqr_hash.h"
#include "iqr_kdf.h"
...
// Create iqr_Context.
// Register hashing algorithms.
...
iqr_retval result = iqr_PBKDF2DeriveKey(context, hash_algorithm,
password, password_size, salt, salt_size, iteration_count,
key_buffer, key_size);
if (result != IQR_OK) {
// Handle error.
}The optional password is pre-determined data shared between all systems
generating keys with PBKDF2. This can be NULL if the password size is also
0 bytes.
Use the salt buffer to provide additional randomness. The salt buffer can be
NULL (and the salt buffer size 0), but providing salt will improve the
security of your application.
Using both a password and a salt provides the best security.
PBKDF2 uses the specified number of iterations to improve the randomness of its derived data at the expense of additional processing time. Use the maximum value that’s tolerable for your application.
The derived key is returned in the key buffer.
Symmetric Encryption
In general, symmetric encryption schemes are not significantly threatened by quantum computers. Doubling the key sizes provides enough security in the face of a quantum threat.
The toolkit provides one symmetric algorithm, RFC-7539’s ChaCha20.
ChaCha20
ChaCha20 (see iqr_chacha20.h) is an easy to use cipher that doesn’t require
additional parameter objects. The key and nonce are provided as byte buffers.
To encrypt data using ChaCha20:
#include "iqr_chacha20.h"
#include "iqr_context.h"
...
// Create iqr_Context. Not strictly needed for ChaCha20, but needed for
// other toolkit APIs.
...
iqr_retval result = iqr_ChaCha20Encrypt(key_buffer, key_size, nonce, nonce_size,
counter, plaintext, plaintext_size, ciphertext, ciphertext_size);
if (result != IQR_OK) {
// Handle error.
}The key buffer must have exactly IQR_CHACHA20_KEY_SIZE bytes of data, and
the nonce buffer must have exactly IQR_CHACHA20_NONCE_SIZE bytes of data.
The key can be pre-shared using a suitable key agreement protocol, and the
nonce should be unique per encryption stream.
Use the counter to indicate the start of this block. Because ChaCha20 is a
block cipher operating in counter mode, you must increment this by
ceiling(plaintext_size / 64) when encrypting additional data using the same
key and nonce.
The ciphertext buffer must be at least as large as the plaintext buffer.
To decrypt data using ChaCha20:
...
result = iqr_ChaCha20Decrypt(key_buffer, key_size, nonce, nonce_size,
counter, ciphertext, ciphertext_size, plaintext, plaintext_size);
if (result != IQR_OK) {
// Handle error.
}The key, nonce, and counter must match the values used to encrypt the data.
Since ChaCha20 is a symmetric cipher, encrypt and decrypt are the same operation, with plaintext and ciphertext swapped.
Digital Signatures
The toolkit provides three digital signature schemes:
Dilithium Signature Scheme
The toolkit provides an implementation of the Dilithium signature scheme as defined in CRYSTALS- Dilithium: Digital Signatures from Module Lattices.
Dilithium comes in two variants:
-
IQR_DILITHIUM_128— 128 bits of quantum security -
IQR_DILITHIUM_160— 160 bits of quantum security
No additional parameters are necessary.
Creating Keys
The toolkit lets you create Dilithium keys after choosing the variant.
To create a Dilithium key pair:
#include "iqr_context.h"
#include "iqr_dilithium.h"
#include "iqr_rng.h"
...
// Create iqr_Context, context.
// Create a Random Number Generator, rng.
...
// Create Dilithium parameters.
iqr_DilithiumParams *params = NULL;
iqr_retval result = iqr_DilithiumCreateParams(context, variant, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
// Create the key pair.
iqr_DilithiumPublicKey *public_key = NULL;
iqr_DilithiumPrivateKey *private_key = NULL;
result = iqr_DilithiumCreateKeyPair(params, rng, &public_key, &private_key);
if (result != IQR_OK) {
// Handle error.
}Signing
To sign a message using the Dilithium private key:
...
size_t signature_size = 0;
result = iqr_DilithiumGetSignatureSize(params, &signature_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *signature = calloc(1, signature_size);
if (signature == NULL) {
// Handle error.
}
result = iqr_DilithiumSign(private_key, rng, index, digest, digest_size,
signature, signature_size);
if (result != IQR_OK) {
// Handle error.
}Verifying Signatures
To verify a signature using the Dilithium public key:
...
result = iqr_DilithiumVerify(public_key, digest, digest_size, signature,
signature_size);
if (result != IQR_OK) {
// Handle error.
}Managing Keys
To export Dilithium keys for storage or transmission:
...
size_t public_key_data_size = 0;
result = iqr_DilithiumGetPublicKeySize(public_key, &public_key_data_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *public_key_data = calloc(1, public_key_data_size);
if (public_key_data == NULL) {
// Handle error.
}
result = iqr_DilithiumExportPublicKey(public_key, public_key_data,
public_key_data_size);
if (result != IQR_OK) {
// Handle error.
}
size_t private_key_data_size = 0;
result = iqr_DilithiumGetPrivateKeySize(private_key, &private_key_data_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *private_key_data = calloc(1, private_key_data_size);
if (private_key_data == NULL) {
// Handle error.
}
result = iqr_DilithiumExportPrivateKey(private_key, private_key_data,
private_key_data_size);
if (result != IQR_OK) {
// Handle error.
}To import Dilithium keys from buffers:
...
// Create iqr_DilithiumParams object using the same variant that was used to
// create the keys.
...
iqr_DilithiumPrivateKey *private_key = NULL;
result = iqr_DilithiumImportPrivateKey(params, private_key_data,
private_key_data_size, &private_key);
if (result != IQR_OK) {
// Handle error.
}
iqr_DilithiumPublicKey *public_key = NULL;
result = iqr_DilithiumImportPublicKey(params, public_key_data, public_key_data_size,
&public_key);
if (result != IQR_OK) {
// Handle error.
}Public Key Format
The data produced by iqr_DilithiumExportPublicKey() follows the format
documented in the CRYSTALS document:
uint8_t seed[32]; // The RNG seed used to create the public key.
uint8_t t1[]; // POLY16 encoded t1 data.Signature Format
The signature produced by iqr_DilithiumSign() follows the format documented
in section 4.1 of the CRYSTALS document:
uint8_t z[];
uint8_t h[];
uint8_t c[];LMS (Leighton-Micali Signature)
The toolkit provides an implementation of the Leighton-Micali Signature (LMS) scheme as defined in the Hash-Based Signatures IETF Draft 7 document.
LMS is a one-time signature scheme that has several major differences from classical digital signature schemes:
-
An LMS private key can only be used to sign a finite number of items.
-
You need to maintain a one-time signature index,
index, carefully.
When you create an LMS key pair, you specify height (iqr_LMSHeight) and
Winternitz (iqr_LMSWinternitz) parameters. The height controls the number of
one-time signatures available in the private key.
The height can be one of:
-
IQR_LMS_HEIGHT_5— 25 (32) one-time signatures -
IQR_LMS_HEIGHT_10— 210 (1024) one-time signatures -
IQR_LMS_HEIGHT_15— 215 (32,768) one-time signatures -
IQR_LMS_HEIGHT_20— 220 (1,048,576) one-time signatures -
IQR_LMS_HEIGHT_25— 225 (33,554,432) one-time signatures
The Winternitz parameter lets you choose a trade-off between speed and size; a larger Winternitz value will give you smaller keys and signatures, but with slower key generation, signing, and verification. The Winternitz value can be one of:
-
IQR_LMS_WINTERNITZ_1 -
IQR_LMS_WINTERNITZ_2 -
IQR_LMS_WINTERNITZ_4— Suggested best time/space trade-off. -
IQR_LMS_WINTERNITZ_8
It’s up to the user to manage domain parameters; the parameter data is not exposed in stored keys or signatures.
The index value, specified when signing, is an index into the one-time
signatures. Re-using a one-time signature destroys the security of the LMS
scheme, so be careful to:
-
Not re-use
indexvalues when signing. -
Safely and securely store your
indexvalue before publishing the signature to protect against software crashes or power loss.
LMS private keys grow larger depending on their height and the Winternitz value used; see the Technical Information section for key sizes. LMS signatures grow relative to the full tree height.
Creating Keys
The toolkit lets you create LMS keys by specifying individual parameters.
To create an LMS key pair:
#include "iqr_context.h"
#include "iqr_hash.h"
#include "iqr_lms.h"
#include "iqr_rng.h"
...
// Create iqr_Context, context.
// Register a SHA2-256 hash algorithm.
// Create a Random Number Generator, rng.
...
// Create LMS parameters.
iqr_LMSParams *params = NULL;
iqr_retval result = iqr_LMSCreateParams(context, winternitz, height,
¶ms);
if (result != IQR_OK) {
// Handle error.
}
// Create the key pair.
iqr_LMSPublicKey *public_key = NULL;
iqr_LMSPrivateKey *private_key = NULL;
result = iqr_LMSCreateKeyPair(params, rng, &public_key, &private_key);
if (result != IQR_OK) {
// Handle error.
}Signing
To sign a message using the LMS private key:
...
size_t signature_size = 0;
result = iqr_LMSGetSignatureSize(params, &signature_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *signature = calloc(1, signature_size);
if (signature == NULL) {
// Handle error.
}
/************************* CRITICALLY IMPORTANT STEP *************************
Before signing, the value of index+1 must be written to non-volatile memory.
Failure to do so could result in a SECURITY BREACH as it could lead to the
re-use of a one-time signature.
This step has been omitted for brevity. Next time you sign, use index+1.
For more information about this property of the LMS private key, please
refer to the LMS specification.
****************************************************************************/
// Retrieve the index's current value.
...
// Store index + 1.
...
result = iqr_LMSSign(private_key, rng, index, message, message_size, signature,
signature_size);
if (result != IQR_OK) {
// Handle error.
}Verifying Signatures
To verify a signature using the LMS public key:
...
result = iqr_LMSVerify(public_key, message, message_size, signature,
signature_size);
if (result != IQR_OK) {
// Handle error.
}Managing Keys
Be sure you’re not using the same private key on different systems, and that
you’re not re-using index values.
To export LMS keys for storage or transmission:
...
size_t public_key_data_size = 0;
result = iqr_LMSGetPublicKeySize(public_key, &public_key_data_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *public_key_data = calloc(1, public_key_data_size);
if (public_key_data == NULL) {
// Handle error.
}
result = iqr_LMSExportPublicKey(public_key, public_key_data,
public_key_data_size);
if (result != IQR_OK) {
// Handle error.
}
size_t private_key_data_size = 0;
result = iqr_LMSGetPrivateKeySize(private_key, &private_key_data_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *private_key_data = calloc(1, private_key_data_size);
if (private_key_data == NULL) {
// Handle error.
}
result = iqr_LMSExportPrivateKey(private_key, private_key_data,
private_key_data_size);
if (result != IQR_OK) {
// Handle error.
}To import LMS keys from buffers:
...
// Create iqr_LMSParams object using the same parameters that were used
// to create the keys.
...
iqr_LMSPrivateKey *private_key = NULL;
result = iqr_LMSImportPrivateKey(params, private_key_data,
private_key_data_size, &private_key);
if (result != IQR_OK) {
// Handle error.
}
iqr_LMSPublicKey *public_key = NULL;
result = iqr_LMSImportPublicKey(params, public_key_data, public_key_data_size,
&public_key);
if (result != IQR_OK) {
// Handle error.
}Public Key Format
The data produced by iqr_LMSExportPublicKey() follows the XDR-inspired
format documented in the
IETF document:
uint32_t ots_type; // The OTS type value (in big-endian form), documented
// in section 4.3 of the IETF document.
uint8_t I[16]; // 16-byte security identifier.
uint8_t public_key[n]; // n bytes of public key.Note that n is always 32 for the toolkit.
Signature Format
The signature produced by iqr_LMSSign() follows the XDR-inspired format
documented in the
IETF document:
uint32_t lms_type; // The LMS type value (in big-endian form), documented
// in section 5.1 of the IETF document.
uint32_t q; // The all-important OTS index.
uint32_t ots_type; // The OTS type value (in big-endian form), documented
// in section 4.3 of the IETF document.
uint8_t C[n]; // n-byte randomizer string.
uint8_t y[n*p]; // n * p bytes OTS signature.
uint8_t path[h*n]; // Height * n bytes of signing path.Note that n is always 32 for the toolkit.
The p value is determined by the n and Winternitz parameters, as defined
in the table of section 4.3 of the
IETF document.
Rainbow Signature Scheme
The toolkit provides an implementation of the Rainbow signature scheme as defined in Rainbow, a New Multivariable Polynomial Signature Scheme.
No parameters are necessary.
Creating Keys
The toolkit lets you create Rainbow keys after creating a random number generator.
To create a Rainbow key pair:
#include "iqr_context.h"
#include "iqr_rainbow.h"
#include "iqr_rng.h"
...
// Create iqr_Context, context.
// Create a Random Number Generator, rng.
...
// Create Rainbow parameters.
iqr_RainbowParams *params = NULL;
iqr_retval result = iqr_RainbowCreateParams(context, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
// Create the key pair.
iqr_RainbowPublicKey *public_key = NULL;
iqr_RainbowPrivateKey *private_key = NULL;
result = iqr_RainbowCreateKeyPair(params, rng, &public_key, &private_key);
if (result != IQR_OK) {
// Handle error.
}Signing
To sign a message using the Rainbow private key:
...
size_t signature_size = IQR_RAINBOW_SIGNATURE_SIZE;
uint8_t *signature = calloc(1, signature_size);
if (signature == NULL) {
// Handle error.
}
result = iqr_RainbowSign(private_key, rng, index, digest, digest_size,
signature, signature_size);
if (result != IQR_OK) {
// Handle error.
}Verifying Signatures
To verify a signature using the Rainbow public key:
...
result = iqr_RainbowVerify(public_key, digest, digest_size, signature,
signature_size);
if (result != IQR_OK) {
// Handle error.
}Managing Keys
To export Rainbow keys for storage or transmission:
...
size_t public_key_data_size = IQR_RAINBOW_PUBLIC_KEY_SIZE;
uint8_t *public_key_data = calloc(1, public_key_data_size);
if (public_key_data == NULL) {
// Handle error.
}
result = iqr_RainbowExportPublicKey(public_key, public_key_data,
public_key_data_size);
if (result != IQR_OK) {
// Handle error.
}
size_t private_key_data_size = IQR_RAINBOW_PRIVATE_KEY_SIZE;
uint8_t *private_key_data = calloc(1, private_key_data_size);
if (private_key_data == NULL) {
// Handle error.
}
result = iqr_RainbowExportPrivateKey(private_key, private_key_data,
private_key_data_size);
if (result != IQR_OK) {
// Handle error.
}To import Rainbow keys from buffers:
...
// Create iqr_RainbowParams object.
...
iqr_RainbowPrivateKey *private_key = NULL;
result = iqr_RainbowImportPrivateKey(params, private_key_data,
private_key_data_size, &private_key);
if (result != IQR_OK) {
// Handle error.
}
iqr_RainbowPublicKey *public_key = NULL;
result = iqr_RainbowImportPublicKey(params, public_key_data,
public_key_data_size, &public_key);
if (result != IQR_OK) {
// Handle error.
}Public Key Format
The data produced by iqr_RainbowExportPublicKey() follows the format
documented in the Rainbow document:
// Two inverted maps plus the central map.
uint8_t map[IQR_RAINBOW_PUBLIC_KEY_SIZE];Signature Format
The signature produced by iqr_RainbowSign() follows the format documented
in the Rainbow document:
uint8_t salted_digest[IQR_SHA2_256_DIGEST_SIZE]; // Salted signature digest.
uint8_t sig[53]; // Signature matrix data.Key Agreement
The toolkit provides four key agreement schemes:
-
ECDH (Elliptic Curve Diffie-Hellman) — an elliptic curve based key agreement scheme
-
LUKE (Lattice based Unique Key Exchange) — an ISARA speed-optimized variant of the NewHope algorithm
-
NewHope — an ideal lattice based key agreement scheme
-
SIDH (Supersingular-Isogeny Diffie-Hellman) — an isogeny based key agreement scheme
ECDH follows a standard Diffie-Hellman protocol between users Alice and Bob:
-
Alice and Bob agree on a set of public parameters.
-
Alice chooses a secret value.
-
Alice uses her secret and the public parameters to calculate a public value.
-
Alice sends the public value to Bob.
-
Bob chooses a secret value.
-
Bob uses his secret and the public parameters to calculate a public value.
-
Bob sends the public value to Alice.
-
Alice uses her secret value and Bob’s public value to calculate the shared secret.
-
Bob uses his secret value and Alice’s public value to calculate the shared secret.
Steps 2-4 for Alice and 5-7 for Bob can be done simultaneously, since the calculations are done independent of the other.
LUKE and NewHope differ from standard Diffie-Hellman. In these schemes, whoever starts the key exchange protocol is the Initiator, and the other is the Responder. The Initiator and the Responder then exchange keys in the following modified manner:
-
The Initiator and the Responder agree on a set of public parameters.
-
The Initiator creates a public/private key pair.
-
The Initiator sends their public key to the Responder.
-
The Responder creates a private key, then uses it and the Initiator’s public key to create their own public key.
-
The Responder sends their public key to the Initiator.
-
The Initiator uses their private key and the Responder’s public key to calculate the shared secret.
-
The Responder uses their private key to calculate the shared secret.
The last two steps can occur simultaneously.
SIDH differs from standard Diffie-Hellman. In SIDH, one end of the connection must be Alice, the other Bob. It doesn’t matter which is which, as long as they’re not the same.
-
Alice creates a private key.
-
Alice uses her private key to derive a public key.
-
Alice sends the public key to Bob.
-
Bob creates a private key.
-
Bob uses his private key to derive a public key.
-
Bob sends the public key to Alice.
-
Alice uses her private key and Bob’s public key to derive the shared secret.
-
Bob uses his private key and Alice’s public key to calculate the shared secret.
Steps 1-3 for Alice and 4-6 for Bob can be done simultaneously, since the calculations are done independent of the other.
|
Note
|
The shared secrets generated by these key agreement schemes are ephemeral. You cannot re-use keys to generate additional shared secrets. |
ECDH
The toolkit provides four elliptic curves for use with ECDH:
-
NIST P-256
-
NIST P-384
-
NIST P-521
-
X25519/Curve25519
It’s up to the user to manage domain parameters; the parameter data is not exposed in stored keys or secrets.
|
Note
|
ECDH is not quantum safe. It’s provided for developers who need to support existing protocols while transitioning to quantum safe algorithms. |
The NIST curves (P-256, P384, and P-521) are defined in FIPS 186-4, Appendix D. Curve25519 is defined in various publications by Daniel J. Bernstein.
Creating Keys
To create a key pair:
#include "iqr_context.h"
#include "iqr_ecdh.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
// The curve can be &IQR_ECDH_NISTP256, &IQR_ECDH_NISTP384, &IQR_ECDH_NISTP521,
// or &IQR_ECDH_X25519 depending on which implementation the other user of ECDH
// is using.
iqr_ECDHParams *params = NULL;
iqr_retval result = iqr_ECDHCreateParams(context, curve, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_ECDHPrivateKey *private_key = NULL;
result = iqr_ECDHCreatePrivateKey(params, rng, &private_key);
if (result != IQR_OK) {
// Handle error.
}
size_t public_key_size = 0;
result = iqr_ECDHGetPublicKeySize(params, &public_key_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *public_key = calloc(1, public_key_size);
if (public_key == NULL) {
// Handle error.
}
result = iqr_ECDHGetPublicKey(private_key, public_key, public_key_size);
if (result != IQR_OK) {
// Handle error.
}
// The public_key can now be sent to the other user of ECDH.
...Generating Secrets
To calculate the shared secret using a received public key:
...
uint8_t *other_public_key = calloc(1, public_key_size);
if (other_public_key == NULL) {
// Handle error.
}
// Receive the other user's public key.
...
size_t shared_secret_size = 0;
result = iqr_ECDHGetSecretSize(params, &shared_secret_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *shared_secret = calloc(1, shared_secret_size);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_ECDHGetSecret(private_key, other_public_key, other_public_key_size,
shared_secret, shared_secret_size);
if (result != IQR_OK) {
// Handle error.
}LUKE
LUKE (Lattice based Unique Key Establishment) is ISARA’s speed-optimized variant of the key agreement scheme presented in the NewHope paper.
Depending on the protocol you’re implementing, either side of the agreement could be acting as Initiator or Responder.
It’s up to the user to manage domain parameters; the parameter data is not exposed in stored keys or secrets.
There is a small (2-60) chance that a LUKE key agreement will fail due to the math involved. To the algorithm, this looks like any other key agreement failure. Start the agreement process over with a new Initiator private key.
Initiator
To create a key pair:
#include "iqr_context.h"
#include "iqr_luke.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
iqr_LUKEParams *params = NULL;
iqr_retval result = iqr_LUKECreateParams(context, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_LUKEInitiatorPrivateKey *private_key = NULL;
result = iqr_LUKECreateInitiatorPrivateKey(params, &private_key);
if (result != IQR_OK) {
// Handle error.
}
size_t public_key_size = IQR_LUKE_INITIATOR_KEY_SIZE;
uint8_t *public_key = calloc(1, public_key_size);
if (public_key == NULL) {
// Handle error.
}
result = iqr_LUKEGetInitiatorPublicKey(private_key, rng,
public_key, public_key_size);
if (result != IQR_OK) {
// Handle error.
}
// The public_key is now sent to the Responder.
...To calculate the shared secret using the Responder’s public key:
...
size_t responder_public_key_size = IQR_LUKE_RESPONDER_KEY_SIZE;
uint8_t *responder_public_key = calloc(1, responder_public_key_size);
if (responder_public_key == NULL) {
// Handle error.
}
// Receive the Responder's public key.
...
size_t shared_secret_size = IQR_LUKE_SECRET_SIZE;
uint8_t *shared_secret = calloc(1, shared_secret_size);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_LUKEGetInitiatorSecret(private_key, responder_public_key,
responder_public_key_size, shared_secret, shared_secret_size);
if (result != IQR_OK) {
// Handle error.
}Responder
To create a key pair using the Initiator’s public key:
#include "iqr_context.h"
#include "iqr_luke.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
size_t initiator_public_key_size = IQR_LUKE_INITIATOR_KEY_SIZE;
uint8_t *initiator_public_key = calloc(1, initiator_public_key_size);
if (inititator_public_key == NULL) {
// Handle error.
}
// Receive the Initiator's public key.
...
iqr_LUKEParams *params = NULL;
iqr_retval result = iqr_LUKECreateParams(context, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_LUKEResponderPrivateKey *private_key = NULL;
result = iqr_LUKECreateResponderPrivateKey(params, &private_key);
if (result != IQR_OK) {
// Handle error.
}
size_t responder_public_key_size = IQR_LUKE_RESPONDER_KEY_SIZE;
uint8_t *responder_public_key = calloc(1, responder_public_key_size);
if (responder_public_key == NULL) {
// Handle error.
}
result = iqr_LUKEGetResponderPublicKey(private_key, rng,
initiator_public_key, initiator_public_key_size, responder_public_key,
responder_public_key_size);
if (result != IQR_OK) {
// Handle error.
}
// Send the Responder's public key to the Initiator.
...To calculate the shared secret using the Responder’s private key:
...
size_t shared_secret_size = IQR_LUKE_SECRET_SIZE;
uint8_t *shared_secret = calloc(1, shared_secret_size);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_LUKEGetResponderSecret(private_key, shared_secret,
shared_secret_size);
if (result != IQR_OK) {
// Handle error.
}
...NewHope
The toolkit provides the NewHope lattice based key agreement scheme.
Depending on the protocol you’re implementing, either side of the agreement could be acting as Initiator or Responder.
It’s up to the user to manage domain parameters; the parameter data is not exposed in stored keys or secrets.
There is a small (2-60) chance that a NewHope key agreement will fail due to the math involved. To the algorithm, this looks like any other key agreement failure. Start the agreement process over with a new Initiator private key.
Initiator
To create a key pair:
#include "iqr_context.h"
#include "iqr_newhope.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
// The variant must be &IQR_NEWHOPE_REFERENCE at this time.
iqr_NewHopeParams *params = NULL;
iqr_retval result = iqr_NewHopeCreateParams(context, &IQR_NEWHOPE_REFERENCE,
¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_NewHopeInitiatorPrivateKey *private_key = NULL;
result = iqr_NewHopeCreateInitiatorPrivateKey(params, &private_key);
if (result != IQR_OK) {
// Handle error.
}
size_t public_key_size = IQR_NEWHOPE_INITIATOR_KEY_SIZE;
uint8_t *public_key = calloc(1, public_key_size);
if (public_key == NULL) {
// Handle error.
}
result = iqr_NewHopeGetInitiatorPublicKey(private_key, rng,
public_key, public_key_size);
if (result != IQR_OK) {
// Handle error.
}
// The public_key is now sent to the Responder.
...To calculate the shared secret using the Responder’s public key:
...
size_t responder_public_key_size = IQR_NEWHOPE_RESPONDER_KEY_SIZE;
uint8_t *responder_public_key = calloc(1, responder_public_key_size);
if (responder_public_key == NULL) {
// Handle error.
}
// Receive the Responder's public key.
...
size_t shared_secret_size = IQR_NEWHOPE_SECRET_SIZE;
uint8_t *shared_secret = calloc(1, shared_secret_size);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_NewHopeGetInitiatorSecret(private_key, responder_public_key,
responder_public_key_size, shared_secret, shared_secret_size);
if (result != IQR_OK) {
// Handle error.
}Responder
To create a key pair using the Initiator’s public key:
#include "iqr_context.h"
#include "iqr_newhope.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
size_t initiator_public_key_size = IQR_NEWHOPE_INITIATOR_KEY_SIZE;
uint8_t *initiator_public_key = calloc(1, initiator_public_key_size);
if (inititator_public_key == NULL) {
// Handle error.
}
// Receive the Initiator's public key.
...
// The variant must be &IQR_NEWHOPE_REFERENCE at this time.
iqr_NewHopeParams *params = NULL;
iqr_retval result = iqr_NewHopeCreateParams(context, &IQR_NEWHOPE_REFERENCE,
¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_NewHopeResponderPrivateKey *private_key = NULL;
result = iqr_NewHopeCreateResponderPrivateKey(params, &private_key);
if (result != IQR_OK) {
// Handle error.
}
size_t responder_public_key_size = IQR_NEWHOPE_RESPONDER_KEY_SIZE;
uint8_t *responder_public_key = calloc(1, responder_public_key_size);
if (responder_public_key == NULL) {
// Handle error.
}
result = iqr_NewHopeGetResponderPublicKey(private_key, rng,
initiator_public_key, initiator_public_key_size, responder_public_key,
responder_public_key_size);
if (result != IQR_OK) {
// Handle error.
}
// Send the Responder's public key to the Initiator.
...To calculate the shared secret using the Responder’s private key:
...
size_t shared_secret_size = IQR_NEWHOPE_SECRET_SIZE;
uint8_t *shared_secret = calloc(1, shared_secret_size);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_NewHopeGetResponderSecret(private_key, shared_secret,
shared_secret_size);
if (result != IQR_OK) {
// Handle error.
}
...SIDH
The toolkit provides the SIDH isogeny based key agreement scheme.
Depending on the protocol you’re implementing, either side of the agreement could be acting as Alice or Bob. It doesn’t matter which is which, as long as they’re not the same.
It’s up to the user to manage domain parameters; the parameter data is not exposed in stored keys or secrets.
Unlike the lattice-based key agreement schemes, Alice and Bob can generate their keys simultaneously, without input from the other side of the transaction.
Alice and Bob are, of course, famous.
Alice
To create a key pair for Alice:
#include "iqr_context.h"
#include "iqr_rng.h"
#include "iqr_sidh.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
iqr_SIDHParams *params = NULL;
iqr_retval result = iqr_SIDHCreateParams(context, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_SIDHAlicePrivateKey *alice_private_key = NULL;
result = iqr_SIDECreateAlicePrivateKey(params, rng, &alice_private_key);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *alice_public_key = calloc(1, IQR_SIDH_ALICE_PUBLIC_KEY_SIZE);
if (alice_public_key == NULL) {
// Handle error.
}
result = iqr_SIDHGetAlicePublicKey(alice_private_key,
alice_public_key, IQR_SIDH_ALICE_PUBLIC_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}
// The alice_public_key is now sent to Bob.
...To calculate the shared secret using Bob’s public key:
...
uint8_t *bob_public_key = calloc(1, IQR_SIDH_BOB_PUBLIC_KEY_SIZE);
if (bob_public_key == NULL) {
// Handle error.
}
// Receive Bob's public key.
...
uint8_t *shared_secret = calloc(1, IQR_SIDH_SECRET_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_SIDHGetAliceSecret(alice_private_key, bob_public_key,
IQR_SIDH_BOB_PUBLIC_KEY_SIZE, shared_secret, IQR_SIDH_SECRET_SIZE);
if (result != IQR_OK) {
// Handle error.
}Bob
To create a key pair for Bob:
#include "iqr_context.h"
#include "iqr_rng.h"
#include "iqr_sidh.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
iqr_SIDHParams *params = NULL;
iqr_retval result = iqr_SIDHCreateParams(context, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_SIDHBobPrivateKey *bob_private_key = NULL;
result = iqr_SIDECreateBobPrivateKey(params, rng, &bob_private_key);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *bob_public_key = calloc(1, IQR_SIDH_BOB_PUBLIC_KEY_SIZE);
if (bob_public_key == NULL) {
// Handle error.
}
result = iqr_SIDHGetBobPublicKey(bob_private_key,
bob_public_key, IQR_SIDH_BOB_PUBLIC_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}
// The bob_public_key is now sent to Alice.
...To calculate the shared secret using Alice’s public key:
...
uint8_t *alice_public_key = calloc(1, IQR_SIDH_ALICE_PUBLIC_KEY_SIZE);
if (alice_public_key == NULL) {
// Handle error.
}
// Receive Alice's public key.
...
uint8_t *shared_secret = calloc(1, IQR_SIDH_SECRET_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_SIDHGetBobSecret(bob_private_key, alice_public_key,
IQR_SIDH_ALICE_PUBLIC_KEY_SIZE, shared_secret, IQR_SIDH_SECRET_SIZE);
if (result != IQR_OK) {
// Handle error.
}Key Encapsulation
The toolkit provides three key encapsulation mechanisms (KEMs):
These schemes let you create and cryptographically encapsulate a symmetric key for safe transmission. They work similar to public key encryption schemes.
To show how Alice and Bob would use a KEM:
-
Bob generates a KEM key pair.
-
Bob sends the KEM public key to Alice.
-
Alice uses Bob’s public key to generate a shared secret and a ciphertext.
-
Alice sends the ciphertext to Bob.
-
Bob uses the KEM’s private key to decapsulate the ciphertext, giving them the original shared secret.
-
Alice and Bob independently derive a private key from the shared secret.
Kyber
The toolkit provides two variants of Kyber:
-
IQR_KYBER_128- 128 bits of quantum security -
IQR_KYBER_224- 224 bits of quantum security
It’s up to the user to manage domain parameters (the Kyber variant); the parameter data is not exposed in stored keys or ciphertexts.
Creating Keys
To create a key pair:
#include "iqr_context.h"
#include "iqr_kyber.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Create a Random Number Generator, rng.
...
// The variant can be IQR_KYBER_128 or IQR_KYBER_224.
iqr_KyberParams *params = NULL;
iqr_retval result = iqr_KyberCreateParams(context, variant, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_KyberPrivateKey *private_key = NULL;
iqr_KyberPublicKey *public_key = NULL;
result = iqr_KyberCreateKeyPair(params, rng, &public_key, &private_key);
if (result != IQR_OK) {
// Handle error.
}
size_t public_key_size = 0;
result = iqr_KyberGetPublicKeySize(params, &public_key_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *public_key_buffer = calloc(1, public_key_size);
if (public_key == NULL) {
// Handle error.
}
result = iqr_KyberExportPublicKey(public_key, public_key_buffer, public_key_size);
if (result != IQR_OK) {
// Handle error.
}
// The public_key can now be sent to other users.
...Encapsulating the Secret
To encapsulate a shared secret using the public key:
uint8_t *shared_secret = calloc(1, IQR_KYBER_SHARED_KEY_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
size_t ciphertext_size = 0;
result = iqr_KyberGetCiphertextSize(params, &ciphertext_size);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *ciphertext = calloc(1, ciphertext_size);
if (ciphertext == NULL) {
// Handle error.
}
result = iqr_KyberEncapsulate(public_key, rng, ciphertext, ciphertext_size,
shared_secret, IQR_KYBER_SHARED_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}
// The ciphertext can now be sent to the recipient.
...Decapsulating the Secret
To decapsulate the shared secret using the private key:
// Get the ciphertext from the sender.
...
size_t ciphertext_size = 0;
result = iqr_KyberGetCiphertextSize(params, &ciphertext_size);
if (result != IQR_OK) {
// Handle error.
}
if (ciphertext_size != received_ciphertext_size) {
// Handle error.
}
uint8_t *shared_secret = calloc(1, IQR_KYBER_SHARED_KEY_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_KyberDecapsulate(private_key, ciphertext, ciphertext_size,
shared_secret, IQR_KYBER_SHARED_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}McEliece KEM
The toolkit provides a McEliece QC-MDPC (Quasi-cyclic medium-density parity check) key encapsulation mechanism.
It’s up to the user to manage domain parameters (the hash algorithm); the parameter data is not exposed in stored keys or ciphertexts.
Creating Keys
To create a key pair:
#include "iqr_context.h"
#include "iqr_hash.h"
#include "iqr_mceliece.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Register the hash algorithm you plan to use.
// Create a Random Number Generator, rng.
...
// You can use any hash algorithm supported by the toolkit.
iqr_McElieceParams *params = NULL;
iqr_retval result = iqr_McElieceCreateParams(context, hash_algo, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_McEliecePrivateKey *private_key = NULL;
iqr_McEliecePublicKey *public_key = NULL;
result = iqr_McElieceCreateKeyPair(params, rng, &public_key, &private_key);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *public_key_buffer = calloc(1, IQR_MCELIECE_PUBLIC_KEY_SIZE);
if (public_key == NULL) {
// Handle error.
}
result = iqr_McElieceExportPublicKey(public_key, public_key_buffer,
IQR_MCELIECE_PUBLIC_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}
// The public_key can now be sent to other users.
...Encapsulating the Secret
To encapsulate a shared secret using the public key:
uint8_t *shared_secret = calloc(1, IQR_MCELIECE_SHARED_KEY_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
uint8_t *ciphertext = calloc(1, IQR_MCELIECE_CIPHERTEXT_SIZE);
if (ciphertext == NULL) {
// Handle error.
}
result = iqr_McElieceEncapsulate(public_key, rng, ciphertext,
IQR_MCELIECE_CIPHERTEXT_SIZE, shared_secret, IQR_MCELIECE_SHARED_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}
// The ciphertext can now be sent to the recipient.
...Decapsulating the Secret
To decapsulate the shared secret using the private key:
// Get the ciphertext from the sender.
...
if (received_ciphertext_size != IQR_MCELIECE_CIPHERTEXT_SIZE) {
// Handle error.
}
uint8_t *shared_secret = calloc(1, IQR_MCELIECE_SHARED_KEY_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_McElieceDecapsulate(private_key, ciphertext,
IQR_MCELIECE_CIPHERTEXT_SIZE, shared_secret, IQR_MCELIECE_SHARED_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}NTRUPrime
The toolkit provides an NTRUPrime key encapsulation mechanism.
No domain parameters are necessary for NTRUPrime; the parameter data is not exposed in stored keys or ciphertexts.
Creating Keys
To create a key pair:
#include "iqr_context.h"
#include "iqr_hash.h"
#include "iqr_ntruprime.h"
#include "iqr_rng.h"
...
// Create an iqr_Context, context.
// Register a SHA3-512 hash implementation.
// Create a Random Number Generator, rng.
...
iqr_NTRUPrimeParams *params = NULL;
iqr_retval result = iqr_NTRUPrimeCreateParams(context, ¶ms);
if (result != IQR_OK) {
// Handle error.
}
iqr_NTRUPrimePrivateKey *private_key = NULL;
iqr_NTRUPrimePublicKey *public_key = NULL;
result = iqr_NTRUPrimeCreateKeyPair(params, rng, &public_key, &private_key);
if (result != IQR_OK) {
// Handle error.
}
uint8_t *public_key_buffer = calloc(1, IQR_NTRUPRIME_PUBLIC_KEY_SIZE);
if (public_key == NULL) {
// Handle error.
}
result = iqr_NTRUPrimeExportPublicKey(public_key, public_key_buffer,
IQR_NTRUPRIME_PUBLIC_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}
// The public_key can now be sent to other users.
...Encapsulating the Secret
To encapsulate a shared secret using the public key:
uint8_t *shared_secret = calloc(1, IQR_NTRUPRIME_SHARED_KEY_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
uint8_t *ciphertext = calloc(1, IQR_NTRUPRIME_CIPHERTEXT_SIZE);
if (ciphertext == NULL) {
// Handle error.
}
result = iqr_NTRUPrimeEncapsulate(public_key, rng, ciphertext,
IQR_NTRUPRIME_CIPHERTEXT_SIZE, shared_secret,
IQR_NTRUPRIME_SHARED_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}
// The ciphertext can now be sent to the recipient.
...Decapsulating the Secret
To decapsulate the shared secret using the private key:
// Get the ciphertext from the sender.
...
if (received_ciphertext_size != IQR_NTRUPRIME_CIPHERTEXT_SIZE) {
// Handle error.
}
uint8_t *shared_secret = calloc(1, IQR_NTRUPRIME_SHARED_KEY_SIZE);
if (shared_secret == NULL) {
// Handle error.
}
result = iqr_NTRUPrimeDecapsulate(private_key, ciphertext,
IQR_NTRUPRIME_CIPHERTEXT_SIZE, shared_secret, IQR_NTRUPRIME_SHARED_KEY_SIZE);
if (result != IQR_OK) {
// Handle error.
}Technical Information
This section provides further information about some technical aspects of the toolkit.
Key and Signature Sizes
Dilithium Keys and Signatures
Dilithium provides 128 or 160 bits of quantum security depending on which variant you use.
Dilithium digital signature scheme key sizes:
| Variant | Public Key (bytes) | Private Key (bytes) |
|---|---|---|
128-bit |
1472 |
15816 |
160-bit |
1760 |
19176 |
Dilithium signs a 64-byte digest, producing these signature sizes:
| Variant | Signature (bytes) |
|---|---|
128-bit |
2700 |
160-bit |
3365 |
Kyber Keys and Ciphertexts
Kyber provides 128 or 224 bits of quantum security depending on which variant you use.
Kyber key encapsulation mechanism key sizes:
| Variant | Public Key (bytes) | Private Key (bytes) |
|---|---|---|
128-bit |
1088 |
2664 |
224-bit |
1440 |
3528 |
Kyber encapsulates a 32-byte shared secret producing these ciphertext sizes:
| Variant | Ciphertext (bytes) |
|---|---|
128-bit |
1184 |
160-bit |
1536 |
LMS Keys and Signatures
LMS is believed to have 256 bits of classical security and 128-bits of quantum security, due to its use of SHA2-256 internally.
The Winternitz parameter has no effect on LMS key sizes.
LMS digital signature scheme key sizes:
| Params | Public Key (bytes) | Private Key (bytes) |
|---|---|---|
h = 5 |
48 |
2,076 |
h = 10 |
48 |
65,564 |
h = 15 |
48 |
2,097,180 |
h = 20 |
48 |
67,108,892 |
h = 25 |
48 |
2,147,483,676 |
| Params | Signature (bytes) |
|---|---|
h = 5, w = 1 |
8676 |
h = 5, w = 2 |
4452 |
h = 5, w = 4 |
2340 |
h = 5, w = 8 |
1284 |
h = 10, w = 1 |
8836 |
h = 10, w = 2 |
4612 |
h = 10, w = 4 |
2500 |
h = 10, w = 8 |
1444 |
h = 15, w = 1 |
8996 |
h = 15, w = 2 |
4772 |
h = 15, w = 4 |
2660 |
h = 15, w = 8 |
1604 |
h = 20, w = 1 |
9156 |
h = 20, w = 2 |
4932 |
h = 20, w = 4 |
2820 |
h = 20, w = 8 |
1764 |
h = 25, w = 1 |
9316 |
h = 25, w = 2 |
5092 |
h = 25, w = 4 |
2980 |
h = 25, w = 8 |
1924 |
McEliece Keys and Ciphertexts
| Variant | Public Key (bytes) | Private Key (bytes) |
|---|---|---|
(none) |
4097 |
8193 |
McEliece encapsulates a 32-byte shared secret producing this ciphertext size:
| Variant | Ciphertext (bytes) |
|---|---|
(none) |
8552 |
NTRUPrime Keys and Ciphertexts
| Variant | Public Key (bytes) | Private Key (bytes) |
|---|---|---|
(none) |
1270 |
4566 |
NTRUPrime encapsulates a 32-byte shared secret producing this ciphertext size:
| Variant | Ciphertext (bytes) |
|---|---|
(none) |
1302 |
Rainbow Keys and Ciphertexts
| Variant | Public Key (bytes) | Private Key (bytes) |
|---|---|---|
(none) |
47520 |
35097 |
Rainbow signs a 64-byte digest producing this signature size:
| Variant | Signature (bytes) |
|---|---|
(none) |
85 |
Build Options
During development of the toolkit, builds use many compiler and linker flags intended to help reduce errors and improve overall code quality.
Compiler Options
When building with clang:
-
-Weverything -Wno-deprecated -Wno-deprecated-declarations -Wno-vla -Wno-packed -Wno-padded -Wno-disabled-macro-expansion -Wno-documentation-unknown-command -Wno-missing-field-initializers
-
-Winline (for everything except Android)
-
-Wno-reserved-id-macro (for everything except FreeBSD)
-
-fno-stack-protector (for Windows, and Cygwin)
-
-fvisibility=hidden
-
-fPIC (for everything except Cygwin)
-
-std=c99
-
-O3
-
-DNDEBUG -D_FORTIFY_SOURCE=2
-
-D__USE_MINGW_ANSI_STDIO=1 (Windows only)
-
-Werror
When building with gcc:
-
-Wall -Wextra -Waggregate-return -Wbad-function-cast -Wcast-align -Wcast-qual -Wfloat-equal -Wformat-security -Wformat=2 -Winit-self -Wmissing-include-dirs -Wmissing-noreturn -Wmissing-prototypes -Wnested-externs -Wno-deprecated -Wno-deprecated-delcarations -Wold-style-definition -Wpedantic -Wredundant-decls -Wshadow -Wstrict-prototypes -Wswitch-default -Wuninitialized -Wunreachable-code -Wunused -Wvarargs -Wwrite-strings
-
-Winline (for everything except Android)
-
-fstrict-aliasing -fstrict-overflow -funsafe-loop-optimizations -fstack-check -fstack-protector-all -fvisibility=hidden -fdata-sections -ffunction-sections
-
-fno-stack-protector (for Windows, and Cygwin)
-
-fPIC (for everything except Cygwin)
-
-pedantic
-
-pipe
-
-std=c99
-
-O3
-
-DNDEBUG -D_FORTIFY_SOURCE=2
-
-D__USE_MINGW_ANSI_STDIO=1 (Windows only)
-
-Werror
Linker Options
When building with clang:
-
-Wl,-undefined,error (for macOS) or -Wl,--no-undefined (others)
When building with gcc:
-
-Wl,-dead_strip (for macOS) or -Wl,--gc-sections (others)
-
-Wl,-undefined,error (for macOS) or -Wl,--no-undefined (others)
Apple Bitcode
The toolkit does not support Apple’s Bitcode for iOS, tvOS, or watchOS binaries. For security reasons, the toolkit needs fine control over optimizations and the life cycle of memory buffers, which isn’t possible when producing Bitcode.
Deprecated APIs
As standards for quantum safe algorithms evolve, the toolkit’s APIs will change to reflect these changes.
If an API is likely to change in the next version of the toolkit, it’ll be
marked with IQR_DEPRECATED in the header. For example:
// From iqr_kdf.h:
#ifndef IQR_IGNORE_1_3_DEPRECATED
IQR_DEPRECATED_MSG("The KDF API will be changing in the next toolkit release.")
#endif
IQR_API
iqr_retval iqr_RFC5869HKDFDeriveKey(const iqr_Context *ctx,
iqr_HashAlgorithmType hash_algo, const uint8_t *salt, size_t salt_size,
const uint8_t *ikm, size_t ikm_size, const uint8_t *info, size_t info_size,
uint8_t *key, size_t key_size);Compiling code that uses iqr_kdf.h will generate a warning (or error if
you’re building with -Werror) so you can plan for the upcoming change.
After you’ve created a task (or user story, or bug) to update the code when
the next version of the toolkit is released, you can add
-DIQR_IGNORE_1_3_DEPRECATED to your compiler flags. This will suppress the
warnings for deprecations in version 1.3 of the toolkit.
Code Stripping
The toolkit has been designed to maximize code stripping, to help when deploying to embedded systems. This is the reasoning behind having no pre-registered default for the hash and RNG algorithms. If you provide your own implementation, or only use a subset of the toolkit’s implementations, your executable won’t include the unused toolkit code.
If your compiler/linker supports it, use the -flto option to enable full
link-time optimization.
Linux libc
The Linux version of the toolkit is built and tested against the following
versions of the libc library:
-
2.23 (Ubuntu, 64-bit)
-
2.24 (Arch, 64-bit)
Building on Windows
When building an application that links against the toolkit static library (libiqr_toolkit_static.lib), add the library under Linker > Input > Additional Dependencies in Visual Studio. No other changes to your Solution file are necessary.
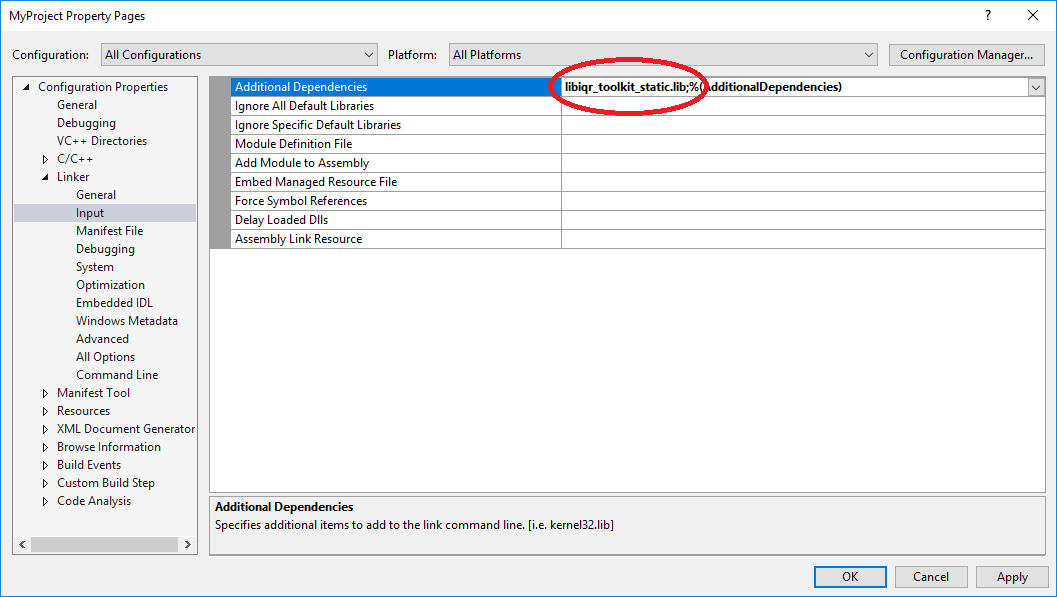
When linking dynamically, you must specify the import library (libiqr_toolkit.lib) under Linker > Input > Additional Dependencies. Additionally, you must add IQR_DLL to the preprocessor listing under C/C++ > Preprocessor > Preprocessor Definitions. This will ensure that extern symbols are imported correctly. The toolkit DLL (libiqr_toolkit.dll) must reside in a location where it can be found by the linker.
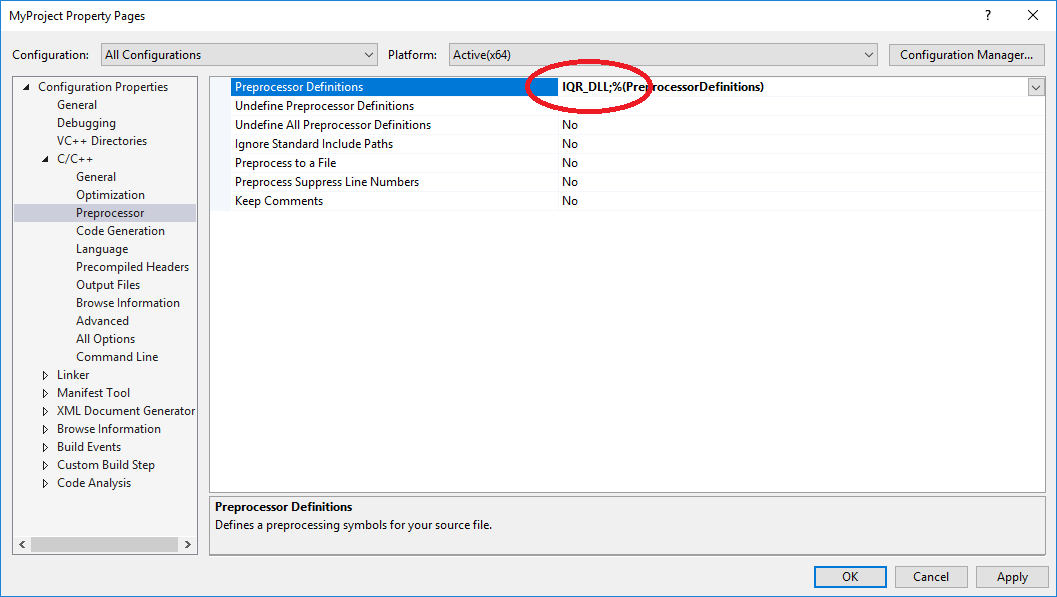
Legal
The ISARA Radiate Security Solution Suite is licensed for use:
Copyright © 2015-2017, ISARA Corporation, All Rights Reserved.
The code and other content set out herein is not in the public domain, is considered a trade secret and is confidential to ISARA Corporation. Use, reproduction or distribution, in whole or in part, of such code or other content is strictly prohibited except by express written permission of ISARA Corporation. Please contact ISARA Corporation at info@isara.com for more information.
Please refer to your sales/support contract for more information about technical support and upgrade entitlements.
Sample Code License
Sample code (and only the sample code) is covered by the Apache 2.0 license:
Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.